Project Requirements - Archaeological Survey of India
Project Requirements - Archaeological Survey of India
Project Requirements - Archaeological Survey of India
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Request for Proposal for establishing e-Governance Systems<br />
proposed solution meets all the requirements <strong>of</strong> the project. For proposed<br />
solutions which are implemented using <strong>of</strong>f-the-shelf solutions available from<br />
reputed vendors, a prototype may not be required.<br />
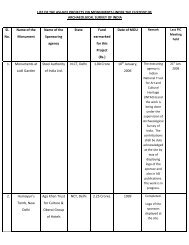
5.7 Phase 6: Entry <strong>of</strong> Historical Data<br />
5.7.1 SI shall be responsible for digitization and migration <strong>of</strong> data for financial planning<br />
and budgeting module from existing data sources to the ASI’s application being<br />
developed as a part <strong>of</strong> this project, to provide for availability <strong>of</strong> all data for the<br />
current financial year.<br />
5.8 Phase 7: Testing and Acceptance<br />
During this phase, SI shall conduct various types <strong>of</strong> testing including:<br />
5.8.1 Application Functional Testing<strong>of</strong> the e‐governance systems shall be carried out to<br />
validate whether the application meets the specified functional requirements<br />
covering the work flows, navigations, and business and data Validation rules for<br />
the defined user categories with access rights. The functional testing should be<br />
done following black box approach and using end‐to‐end user scenarios.<br />
5.8.2 Application Usability Testing shall include systematic observation under controlled<br />
conditions to determine how well users can use the application. The proposed<br />
systems are likely to be used by users <strong>of</strong> different levels <strong>of</strong> computer knowledge.<br />
Usability testing will ensure that the all types <strong>of</strong> users are comfortable to use the<br />
system. This shall be done by using defined international standards which<br />
recommend extensive user interaction and analysis <strong>of</strong> userbehavior for a defined<br />
task.<br />
5.8.1 Performance Testing <strong>of</strong> the system shall be done to ensure that system is capable<br />
<strong>of</strong> handling defined user as well as transactional load. The performance testing <strong>of</strong><br />
the e‐governance system will include measuring the response time <strong>of</strong> the system<br />
for defined scenarios. Also the manner/ trend in which performance changes with<br />
load will determine the scalability <strong>of</strong> the e‐governance systems.<br />
5.8.2 Application Security Testing conducted to unearth various application security<br />
vulnerabilities, weaknesses and concerns related to Data /Input Validation,<br />
Authentication, Authorization /Access Control, Session Management, Error<br />
Handling, Use <strong>of</strong> Cryptography, etc. Typical issues which may be discovered in an<br />
application security testing include Cross‐site scripting, Broken ACLs/Weak<br />
passwords, Weak session management, Buffer overflows, Forceful browsing,<br />
Form/hidden field manipulation, Command injection, SQL injection, Cookie<br />
poisoning, Insecure use <strong>of</strong> cryptography, Mis‐configurations, Well‐known platform<br />
vulnerabilities, Errors triggering sensitive information leak etc.<br />
5.8.3 Penetration Testing shall be done remotely from public domain (Internet) and also<br />
RFP Volume 1:<strong>Project</strong> <strong>Requirements</strong> P a g e | 17