automatically exploiting cross-invocation parallelism using runtime ...
automatically exploiting cross-invocation parallelism using runtime ...
automatically exploiting cross-invocation parallelism using runtime ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
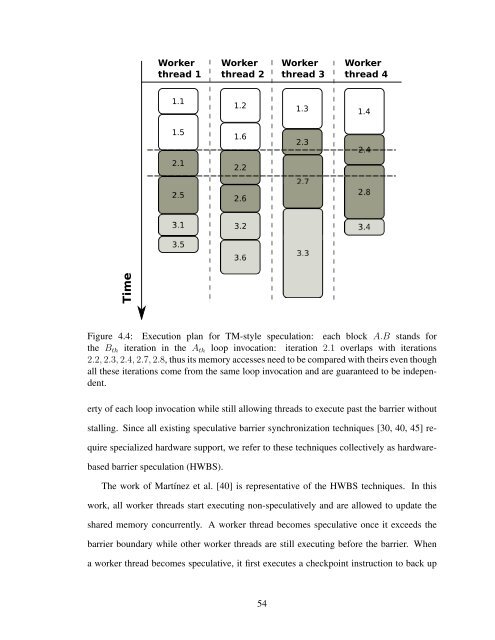
Workerthread 1Workerthread 2Workerthread 3Workerthread 41.11.2 1.3 1.41.51.62.32.42.12.23.13.23.43.53.3TimeFigure 4.4: Execution plan for TM-style speculation: each block A.B stands forthe B th iteration in the A th loop <strong>invocation</strong>: iteration 2.1 overlaps with iterations2.2, 2.3, 2.4, 2.7, 2.8, thus its memory accesses need to be compared with theirs even thoughall these iterations come from the same loop <strong>invocation</strong> and are guaranteed to be independent.erty of each loop <strong>invocation</strong> while still allowing threads to execute past the barrier withoutstalling. Since all existing speculative barrier synchronization techniques [30, 40, 45] requirespecialized hardware support, we refer to these techniques collectively as hardwarebasedbarrier speculation (HWBS).The work of Martínez et al. [40] is representative of the HWBS techniques. In thiswork, all worker threads start executing non-speculatively and are allowed to update theshared memory concurrently. A worker thread becomes speculative once it exceeds thebarrier boundary while other worker threads are still executing before the barrier. Whena worker thread becomes speculative, it first executes a checkpoint instruction to back up54