Biometric Template Protection - NIST Visual Image Processing Group
Biometric Template Protection - NIST Visual Image Processing Group Biometric Template Protection - NIST Visual Image Processing Group
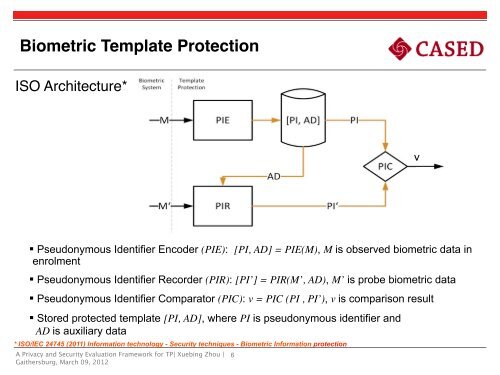
Biometric Template ProtectionISO Architecture*! !v§ Pseudonymous Identifier Encoder (PIE): [PI, AD] = PIE(M), M is observed biometric data inenrolment§ Pseudonymous Identifier Recorder (PIR): [PI’] = PIR(M’, AD), M’ is probe biometric data§ Pseudonymous Identifier Comparator (PIC): v = PIC (PI , PI’), v is comparison result§ Stored protected template [PI, AD], where PI is pseudonymous identifier andAD is auxiliary data* ISO/IEC 24745 (2011) Information technology - Security techniques - Biometric Information protectionA Privacy and Security Evaluation Framework for TP| Xuebing Zhou |Gaithersburg, March 09, 20126
How to Assess Template Protection§ Protection goals - Evaluation criteria§ Security of PI: Hardness to find an M* (“pre-image” of PI), which can passPI- verification process§ Privacy protection ability:§ Irreversibility: Hardness to find an M*, which is very close to the original M§ Privacy leakage: Information about M contained in protected templates§ Unlinkability:§Cross matching: Personal identifiable information contained inprotected templates§Leakage amplification: Additional information about M or pre-image of PI gainedwhen combining protected templates of the same subjectA Privacy and Security Evaluation Framework for TP| Xuebing Zhou |Gaithersburg, March 09, 20127
- Page 1 and 2: A Generalized Framework forPrivacy
- Page 3 and 4: Biometric Systems§ Privacy and sec
- Page 5 and 6: Biometric Template ProtectionA Priv
- Page 7 and 8: Biometric Template ProtectionPT1PT2
- Page 9 and 10: Biometric Template ProtectionPT1PT2
- Page 11 and 12: Biometric Template ProtectionPT1PT2
- Page 13: State of the Art of Template Protec
- Page 17 and 18: How to Assess Template ProtectionEv
- Page 19 and 20: How to Assess Template Protection§
- Page 21 and 22: Assessment of Different Protected S
- Page 23 and 24: Assessment of Different Protected S
- Page 25 and 26: Conclusions§ The framework is usef
- Page 27 and 28: References§ Zhou, Xuebing: “Priv
<strong>Biometric</strong> <strong>Template</strong> <strong>Protection</strong>ISO Architecture*! !v§ Pseudonymous Identifier Encoder (PIE): [PI, AD] = PIE(M), M is observed biometric data inenrolment§ Pseudonymous Identifier Recorder (PIR): [PI’] = PIR(M’, AD), M’ is probe biometric data§ Pseudonymous Identifier Comparator (PIC): v = PIC (PI , PI’), v is comparison result§ Stored protected template [PI, AD], where PI is pseudonymous identifier andAD is auxiliary data* ISO/IEC 24745 (2011) Information technology - Security techniques - <strong>Biometric</strong> Information protectionA Privacy and Security Evaluation Framework for TP| Xuebing Zhou |Gaithersburg, March 09, 20126