CIPUG Morgan King Virtualization
CIPUG Morgan King Virtualization
CIPUG Morgan King Virtualization
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
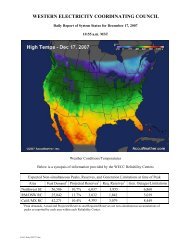
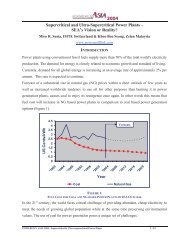
CIP-005-3Electronic Security Perimeter• Is an ESP identified?• Does every virtualized CCA reside within anESP?• Are any virtualized Cyber Assets used inAccess Control and/or Monitoring of ESP(R1.5)?• Do any Hosts and VMs connect to a non-ESP network?23