hp-security-research-cyber-risk-report-pdf-2-w-1408
hp-security-research-cyber-risk-report-pdf-2-w-1408
hp-security-research-cyber-risk-report-pdf-2-w-1408
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
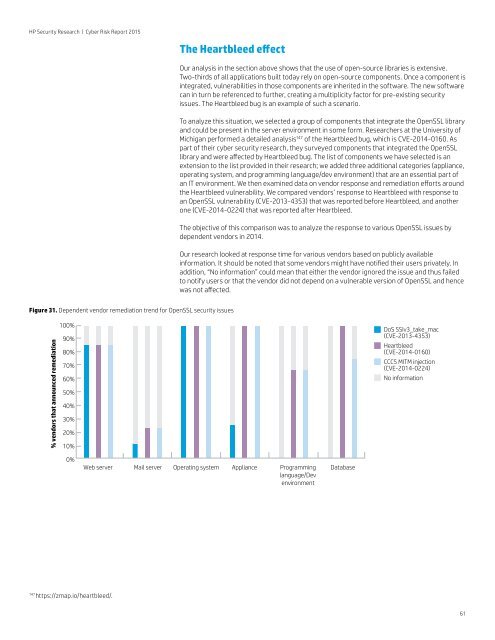
HP Security Research | Cyber Risk Report 2015The Heartbleed effectOur analysis in the section above shows that the use of open-source libraries is extensive.Two-thirds of all applications built today rely on open-source components. Once a component isintegrated, vulnerabilities in those components are inherited in the software. The new softwarecan in turn be referenced to further, creating a multiplicity factor for pre-existing <strong>security</strong>issues. The Heartbleed bug is an example of such a scenario.To analyze this situation, we selected a group of components that integrate the OpenSSL libraryand could be present in the server environment in some form. Researchers at the University ofMichigan performed a detailed analysis 147 of the Heartbleed bug, which is CVE-2014-0160. Aspart of their <strong>cyber</strong> <strong>security</strong> <strong>research</strong>, they surveyed components that integrated the OpenSSLlibrary and were affected by Heartbleed bug. The list of components we have selected is anextension to the list provided in their <strong>research</strong>; we added three additional categories (appliance,operating system, and programming language/dev environment) that are an essential part ofan IT environment. We then examined data on vendor response and remediation efforts aroundthe Heartbleed vulnerability. We compared vendors’ response to Heartbleed with response toan OpenSSL vulnerability (CVE-2013-4353) that was <strong>report</strong>ed before Heartbleed, and anotherone (CVE-2014-0224) that was <strong>report</strong>ed after Heartbleed.The objective of this comparison was to analyze the response to various OpenSSL issues bydependent vendors in 2014.Our <strong>research</strong> looked at response time for various vendors based on publicly availableinformation. It should be noted that some vendors might have notified their users privately. Inaddition, “No information” could mean that either the vendor ignored the issue and thus failedto notify users or that the vendor did not depend on a vulnerable version of OpenSSL and hencewas not affected.Figure 31. Dependent vendor remediation trend for OpenSSL <strong>security</strong> issues% vendors that announced remediation100%90%80%70%60%50%40%30%20%10%DoS SSIv3_take_mac(CVE-2013-4353)Heartbleed(CVE-2014-0160)CCCS MITM injection(CVE-2014-0224)No information0%Web server Mail server Operating system Appliance Programminglanguage/DevenvironmentDatabase147https://zmap.io/heartbleed/.61