hp-security-research-cyber-risk-report-pdf-2-w-1408
hp-security-research-cyber-risk-report-pdf-2-w-1408
hp-security-research-cyber-risk-report-pdf-2-w-1408
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
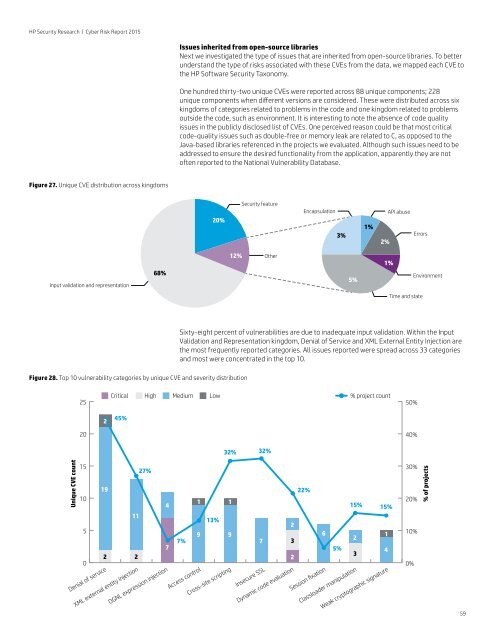
HP Security Research | Cyber Risk Report 2015Issues inherited from open-source librariesNext we investigated the type of issues that are inherited from open-source libraries. To betterunderstand the type of <strong>risk</strong>s associated with these CVEs from the data, we mapped each CVE tothe HP Software Security Taxonomy.One hundred thirty-two unique CVEs were <strong>report</strong>ed across 88 unique components; 228unique components when different versions are considered. These were distributed across sixkingdoms of categories related to problems in the code and one kingdom related to problemsoutside the code, such as environment. It is interesting to note the absence of code qualityissues in the publicly disclosed list of CVEs. One perceived reason could be that most criticalcode-quality issues such as double-free or memory leak are related to C, as opposed to theJava-based libraries referenced in the projects we evaluated. Although such issues need to beaddressed to ensure the desired functionality from the application, apparently they are notoften <strong>report</strong>ed to the National Vulnerability Database.Figure 27. Unique CVE distribution across kingdoms20%Security featureEncapsulation3%1%2%API abuseErrorsInput validation and representation68%12%Other5%1%EnvironmentTime and stateSixty-eight percent of vulnerabilities are due to inadequate input validation. Within the InputValidation and Representation kingdom, Denial of Service and XML External Entity Injection arethe most frequently <strong>report</strong>ed categories. All issues <strong>report</strong>ed were spread across 33 categoriesand most were concentrated in the top 10.Figure 28. Top 10 vulnerability categories by unique CVE and severity distribution25Critical High Medium Low% project count50%245%2040%32% 32%Unique CVE count151050Denial of service27%191 141113%9 97%72 2XML external entity injectionOGNL expression injectionAccess controlCross-site scriptingInsecure SSL22%15% 15%2617325%432Dynamic code evaluationSession fixationClassloader manipulationWeak cryptographic signature30%20%10%0%% of projects59