hp-security-research-cyber-risk-report-pdf-2-w-1408
hp-security-research-cyber-risk-report-pdf-2-w-1408
hp-security-research-cyber-risk-report-pdf-2-w-1408
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
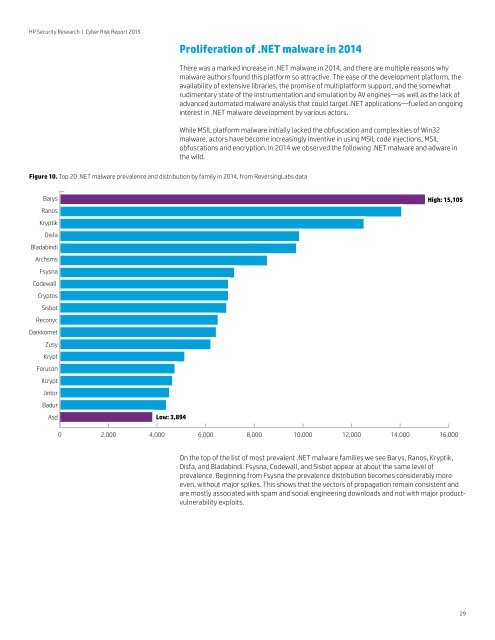
HP Security Research | Cyber Risk Report 2015Proliferation of .NET malware in 2014There was a marked increase in .NET malware in 2014, and there are multiple reasons whymalware authors found this platform so attractive. The ease of the development platform, theavailability of extensive libraries, the promise of multiplatform support, and the somewhatrudimentary state of the instrumentation and emulation by AV engines—as well as the lack ofadvanced automated malware analysis that could target .NET applications—fueled an ongoinginterest in .NET malware development by various actors.While MSIL platform malware initially lacked the obfuscation and complexities of Win32malware, actors have become increasingly inventive in using MSIL code injections, MSILobfuscations and encryption. In 2014 we observed the following .NET malware and adware inthe wild.Figure 10. Top 20 .NET malware prevalence and distribution by family in 2014, from ReversingLabs dataBarysRanosKryptikDisfaBladabindiArchsmsFsysnaCodewallCryptosSisbotReconycDarkkometZusyKryptForuconIlcryptJintorBadurAsdLow: 3,894High: 15,1050 2,000 4,000 6,000 8,000 10,000 12,000 14,000 16,000On the top of the list of most prevalent .NET malware families we see Barys, Ranos, Kryptik,Disfa, and Bladabindi. Fsysna, Codewall, and Sisbot appear at about the same level ofprevalence. Beginning from Fsysna the prevalence distribution becomes considerably moreeven, without major spikes. This shows that the vectors of propagation remain consistent andare mostly associated with spam and social engineering downloads and not with major productvulnerabilityexploits.29