Design and Test of a Scalable Security Processor - ACM Digital ...
Design and Test of a Scalable Security Processor - ACM Digital ...
Design and Test of a Scalable Security Processor - ACM Digital ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
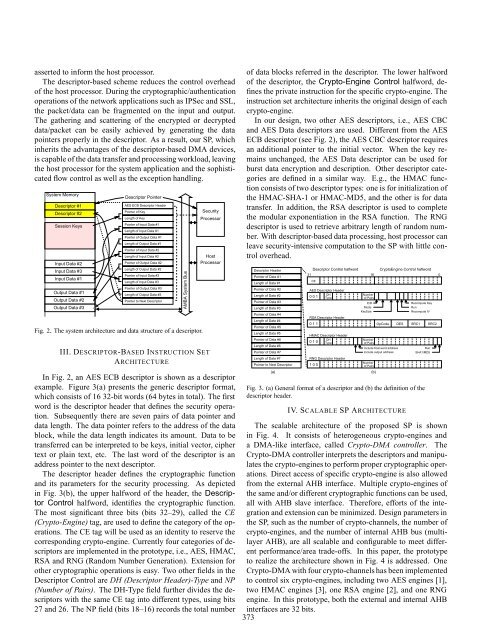
asserted to inform the host processor.The descriptor-based scheme reduces the control overhead<strong>of</strong> the host processor. During the cryptographic/authenticationoperations <strong>of</strong> the network applications such as IPSec <strong>and</strong> SSL,the packet/data can be fragmented on the input <strong>and</strong> output.The gathering <strong>and</strong> scattering <strong>of</strong> the encrypted or decrypteddata/packet can be easily achieved by generating the datapointers properly in the descriptor. As a result, our SP, whichinherits the advantages <strong>of</strong> the descriptor-based DMA devices,is capable <strong>of</strong> the data transfer <strong>and</strong> processing workload, leavingthe host processor for the system application <strong>and</strong> the sophisticatedflow control as well as the exception h<strong>and</strong>ling.System MemoryDescriptor #1Descriptor #2Session KeysInput Data #2Input Data #3Input Data #1Output Data #1Output Data #2Output Data #3Descriptor PointerAES ECB Descriptor HeaderPointer <strong>of</strong> KeyLength <strong>of</strong> KeyPointer <strong>of</strong> Input Data #1Length <strong>of</strong> Input Data #1Pointer <strong>of</strong> Output Data #1Length <strong>of</strong> Output Data #1Pointer <strong>of</strong> Input Data #2Length <strong>of</strong> Input Data #2Pointer <strong>of</strong> Output Data #2Length <strong>of</strong> Output Data #2Pointer <strong>of</strong> Input Data #3Length <strong>of</strong> Input Data #3Pointer <strong>of</strong> Output Data #3Length <strong>of</strong> Output Data #3Pointer to Next DescriptorFig. 2. The system architecture <strong>and</strong> data structure <strong>of</strong> a descriptor.III. DESCRIPTOR-BASED INSTRUCTION SETARCHITECTUREAMBA System Bus<strong>Security</strong><strong>Processor</strong>Host<strong>Processor</strong>In Fig. 2, an AES ECB descriptor is shown as a descriptorexample. Figure 3(a) presents the generic descriptor format,which consists <strong>of</strong> 16 32-bit words (64 bytes in total). The firstword is the descriptor header that defines the security operation.Subsequently there are seven pairs <strong>of</strong> data pointer <strong>and</strong>data length. The data pointer refers to the address <strong>of</strong> the datablock, while the data length indicates its amount. Data to betransferred can be interpreted to be keys, initial vector, ciphertext or plain text, etc. The last word <strong>of</strong> the descriptor is anaddress pointer to the next descriptor.The descriptor header defines the cryptographic function<strong>and</strong> its parameters for the security processing. As depictedin Fig. 3(b), the upper halfword <strong>of</strong> the header, the DescriptorControl halfword, identifies the cryptographic function.The most significant three bits (bits 32–29), called the CE(Crypto-Engine) tag, are used to define the category <strong>of</strong> the operations.The CE tag will be used as an identity to reserve thecorresponding crypto-engine. Currently four categories <strong>of</strong> descriptorsare implemented in the prototype, i.e., AES, HMAC,RSA <strong>and</strong> RNG (R<strong>and</strong>om Number Generation). Extension forother cryptographic operations is easy. Two other fields in theDescriptor Control are DH (Descriptor Header)-Type <strong>and</strong> NP(Number <strong>of</strong> Pairs). The DH-Type field further divides the descriptorswith the same CE tag into different types, using bits27 <strong>and</strong> 26. The NP field (bits 18–16) records the total number<strong>of</strong> data blocks referred in the descriptor. The lower halfword<strong>of</strong> the descriptor, the Crypto-Engine Control halfword, definesthe private instruction for the specific crypto-engine. Theinstruction set architecture inherits the original design <strong>of</strong> eachcrypto-engine.In our design, two other AES descriptors, i.e., AES CBC<strong>and</strong> AES Data descriptors are used. Different from the AESECB descriptor (see Fig. 2), the AES CBC descriptor requiresan additional pointer to the initial vector. When the key remainsunchanged, the AES Data descriptor can be used forburst data encryption <strong>and</strong> description. Other descriptor categoriesare defined in a similar way. E.g., the HMAC functionconsists <strong>of</strong> two descriptor types: one is for initialization <strong>of</strong>the HMAC-SHA-1 or HMAC-MD5, <strong>and</strong> the other is for datatransfer. In addition, the RSA descriptor is used to completethe modular exponentiation in the RSA function. The RNGdescriptor is used to retrieve arbitrary length <strong>of</strong> r<strong>and</strong>om number.With descriptor-based data processing, host processor canleave security-intensive computation to the SP with little controloverhead.Descriptor HeaderPointer <strong>of</strong> Data #1Length <strong>of</strong> Data #1Pointer <strong>of</strong> Data #2Length <strong>of</strong> Data #2Pointer <strong>of</strong> Data #3Length <strong>of</strong> Data #3Pointer <strong>of</strong> Data #4Length <strong>of</strong> Data #4Pointer <strong>of</strong> Data #5Length <strong>of</strong> Data #5Pointer <strong>of</strong> Data #6Length <strong>of</strong> Data #6Pointer <strong>of</strong> Data #7Length <strong>of</strong> Data #7Pointer to Next Descriptor(a)Descriptor Control halfwordCryptoEngine Control haflword31 16 0CEAES Descriptor HeaderDH0 0 1 TypeRSA Descriptor Header0 1 1HMAC Descriptor HeaderDH0 1 0 TypeRNG Descriptor Header1 0 0Number<strong>of</strong> PairsE/DModeKeySizeNumber<strong>of</strong> Pairs(b)OpCodeNumber<strong>of</strong> PairsInclude final word addressinclude output addressDESRecompute KeyRunRecompute IVSRC1RunSHA1/MD5Fig. 3. (a) General format <strong>of</strong> a descriptor <strong>and</strong> (b) the definition <strong>of</strong> thedescriptor header.IV. SCALABLE SP ARCHITECTUREThe scalable architecture <strong>of</strong> the proposed SP is shownin Fig. 4. It consists <strong>of</strong> heterogeneous crypto-engines <strong>and</strong>a DMA-like interface, called Crypto-DMA controller. TheCrypto-DMA controller interprets the descriptors <strong>and</strong> manipulatesthe crypto-engines to perform proper cryptographic operations.Direct access <strong>of</strong> specific crypto-engine is also allowedfrom the external AHB interface. Multiple crypto-engines <strong>of</strong>the same <strong>and</strong>/or different cryptographic functions can be used,all with AHB slave interface. Therefore, efforts <strong>of</strong> the integration<strong>and</strong> extension can be minimized. <strong>Design</strong> parameters inthe SP, such as the number <strong>of</strong> crypto-channels, the number <strong>of</strong>crypto-engines, <strong>and</strong> the number <strong>of</strong> internal AHB bus (multilayerAHB), are all scalable <strong>and</strong> configurable to meet differentperformance/area trade-<strong>of</strong>fs. In this paper, the prototypeto realize the architecture shown in Fig. 4 is addressed. OneCrypto-DMA with four crypto-channels has been implementedto control six crypto-engines, including two AES engines [1],two HMAC engines [3], one RSA engine [2], <strong>and</strong> one RNGengine. In this prototype, both the external <strong>and</strong> internal AHBinterfaces are 32 bits.373SRC2