Department of IT - IFET College of Engineering
Department of IT - IFET College of Engineering
Department of IT - IFET College of Engineering
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
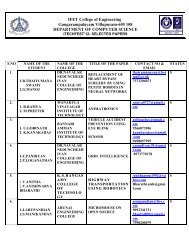
<strong>IFET</strong> COLLEGE OF ENGINEERINGDEPARTMENT OF INFORMATION TECHNOLOGYTECHNOVISION’12Adro<strong>IT</strong> 2K12LIST OF RECEIVED PAPERSS.NO YEAR NAME OF THE STUDENT T<strong>IT</strong>LE OF PAPER1. III S.POOJA DEVI Unlicensed Mobile Access2. III S.RANJANI Steganography3. III K.THAMIZHARASI Stealth Virus4. III M.SHEIK AMEEN OS virtualization5. III P.RAJESWARI Wireless Network Security6. III K.RAMYA Finger Printing Technology7. III K.BEULAH Nano Robots8. III R.PRAVEENA Unlicensed Mobile Access9. III S.GIRIJA N-RAM Technology10. III R.RATHIDEVI Ovonic Unified Memory11. III V.SHARMILA Agent Based System12. III N.KR<strong>IT</strong>HIGA Web services seminar usingsemantics description13. III C.PRABHAVATHI Survivable Network –Embedded14. III T.CHANDRASEKAR Wi-Max MIMOSystem based automatic pancreaticcell simulator for diabetes control15. III P.VENKATRAJ Advance air force using WARMRobotics16. III P.NARESH KUMAR JIRO Technology
17. III T.PERUMAL JIRO Technology18. III B.NIRANJAN Stealth Virus19. III A.BALAJI Agent Based System20. III S.SARATHLUMAR Mobile Hoc Network21. III ANAND.K Red Tacton22. III MANIKANDAN.P Multi-modal agent based mobileroute advisory system for PTS23. II A.NAZIYA BANUBlue Eye TechnologyA.ANANDHI24. II K.NANDHININano MedicineB.MALATHI25. II R.SARANYADEVIIsolation <strong>of</strong> dead chicken PoultryS.KAV<strong>IT</strong>HA26. II U.HELEN AISHWARYA Image processingS.YOGALAKSHMI27. II V.ARUNKUMARInfini BandD.PRAVEENA28. II T.KOTHAIStealth virusS.SONEIYA29. II S.SUBASREEJIRO TechnologyM.PRABA30. II R.VENNILA. GSM31. II K.REVATHYR.AM<strong>IT</strong>HAVARSHA32. II J.N<strong>IT</strong>HYA MARIAS.JAYALAKSHMI33. II M.VASANTHAPRIYAJ.SOWNDARYANetwork SecuritySuper Worms and CrytpvirologyMIMO communication
34. II PUNNIYAPALM Vein AuthenticationBEN SANDRA35. II M.MEGALAGreen ComputingJ.THAMIMUNISA36. II K.VENGATACHALAPATHY Network SecurityM.SATHISH37. II A.BALAJINano robots in HIVAMIRTHA GANESH38. II P.SARANARAYANAN 5G mobilesS.AMIRTHAGANESH39. II D.KRISHNA KUMAR 4GL.RAJESH KUMAR40. II A.MOHAMED IMRAN ALI Ethical HackingM.JEEVAMUTHAN41. II S.SELVAKUMARCARONM.BENSON42. II R.PRATHEEBARed TactonM.NANDHINI43. II A.ANISH KANNAS.MARIAPRAGASAMSniffer tool for mobileLost44. II R.N<strong>IT</strong>HIANANDHAM Artificial VisionP.VALLAL PERUMAL45. II D.GOPINATHCellular NetworkMANIKANADAN46. II V.BHARATHY Network Security47. II K.MONICA FENCYNetwork management SystemsK.N<strong>IT</strong>HIYA48. II R.RAJESH KUMAR Digital Object identifier
49. IV B.SHINY ANGELINE Authentication schemes for sessionpassword using colors and images50. IV E.MANOLAKSHMI Digital watermarking for tamperpro<strong>of</strong>ing and authentication inimages51. IV B.ASHWINI High Quality Reflection separationusing polarized images52. IV E.AKILA Multicast authentication in smartgrid using time Signature53. IV J.DIVINE FREEDA Media cloud in cloud computingusing .NET
<strong>IFET</strong> COLLEGE OF ENGINEERINGDEPARTMENT OF INFORMATION TECHNOLOGYTECHNOVISION’12Adro<strong>IT</strong> 2K12LIST OF SELECTED PAPERSS.NO YEAR NAME OF THE T<strong>IT</strong>LE OF PAPERSTUDENT1. III C.PRABHAVATHI Survivable Network2. III T.CHANDRASEKAR Wi-Max MIMO3. III P.VENKATRAJ Advance air force using WARM Robotics4. III B.NIRANJAN Stealth Virus5. III ANAND.K Red Tacton6. III S.SARATHLUMAR Mobile Hoc Network7. II A.NAZIYA BANUA.ANANDHI8. II V.ARUNKUMARD.PRAVEENA9. II J.N<strong>IT</strong>HYA MARIAS.JAYALAKSHMI10. II M.VASANTHAPRIYAJ.SOWNDARYA11. II PUNNIYABEN SANDRA12. II P.SARANARAYANANS.AMIRTHAGANESH13. II S.SELVAKUMARM.BENSON14. II A.ANISH KANNAS.MARIAPRAGASAM15. II D.GOPINATHMANIKANADANBlue Eye TechnologyInfini -BandSuper Worms and CrytpovirologyMIMO communicationPALM Vein Authentication5G mobilesCARONSniffer Tool for mobile lostCellular Network
16. II U.HELEN AISHWARYA Image processingS.YOGALAKSHMI17. IV E.MANOLAKSHMI Digital watermarking for tamper pro<strong>of</strong>ingand authentication in images18. IV B.ASHWINI High Quality Reflection separation usingpolarized imagesNo <strong>of</strong> papers Received: 53No <strong>of</strong> papers short listed: 18Faculty Committee MembersTechnical committeeMr.U.Palani ,AP HOD/<strong>IT</strong>Mrs L.Mary Shyamala ,SLMs.Jenny Kalaiarasi,SLJ.Jayachitra,LecturerMs.A.Arthibala, LecturerS.Saranya,LecturerA.Sarkunavathi,LecturerS.Sasikala,LecturerEvent-Coordinators:Ms.Jenny Kalaiarasi,SLMrs.K.Elavarasi,LecturerMs.R.Illamathi Devi,LecturerComperingMs.G.Kavitha, LecturerMs.C.Nancy Nightingale,LecturerVenue arrangementMr.V.Rajapandiyan, LecturerMs.M.Kayathri, LecturerStudent VolunteersSymposium CoordinatorsA.BALAJI, III <strong>IT</strong>K.THAMIZHARASI, III <strong>IT</strong>V.SHARMILA, III <strong>IT</strong>GANESH.S, II <strong>IT</strong>
MEGALA.M, II <strong>IT</strong>Event CoordinatorsS.POOJA DEVI, III <strong>IT</strong>NARESHKUMAR.P, III <strong>IT</strong>SUSIPADHMADEVI.U, III <strong>IT</strong>SARATH KUMAR.S, III <strong>IT</strong>MONICA FENCY.K, II <strong>IT</strong>Internal Symposium coordinator: A.Sarkunavathi Lec/<strong>IT</strong>