Migration of a Chosen Architectural Pattern to Service Oriented ...
Migration of a Chosen Architectural Pattern to Service Oriented ... Migration of a Chosen Architectural Pattern to Service Oriented ...
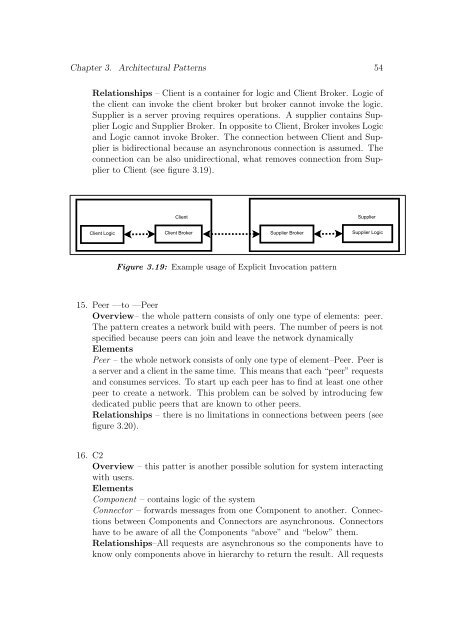
Chapter 3. Architectural Patterns 54Relationships – Client is a container for logic and Client Broker. Logic ofthe client can invoke the client broker but broker cannot invoke the logic.Supplier is a server proving requires operations. A supplier contains SupplierLogic and Supplier Broker. In opposite to Client, Broker invokes Logicand Logic cannot invoke Broker. The connection between Client and Supplieris bidirectional because an asynchronous connection is assumed. Theconnection can be also unidirectional, what removes connection from Supplierto Client (see figure 3.19).Client SupplierClient Logic Client Broker Supplier Broker Supplier LogicFigure 3.19: Example usage of Explicit Invocation pattern15. Peer —to —PeerOverview– the whole pattern consists of only one type of elements: peer.The pattern creates a network build with peers. The number of peers is notspecified because peers can join and leave the network dynamicallyElementsPeer – the whole network consists of only one type of element–Peer. Peer isa server and a client in the same time. This means that each “peer” requestsand consumes services. To start up each peer has to find at least one otherpeer to create a network. This problem can be solved by introducing fewdedicated public peers that are known to other peers.Relationships – there is no limitations in connections between peers (seefigure 3.20).16. C2Overview – this patter is another possible solution for system interactingwith users.ElementsComponent – contains logic of the systemConnector – forwards messages from one Component to another. Connectionsbetween Components and Connectors are asynchronous. Connectorshave to be aware of all the Components “above” and “below” them.Relationships–All requests are asynchronous so the components have toknow only components above in hierarchy to return the result. All requests
Chapter 3. Architectural Patterns 55Peer 4Peer 1Peer 3Peer 2Figure 3.20: Example usage of Peer–to–Peer patternto lower components are forwarded by connecting layers and componentsdo not care which exactly sub–agent will execute it. Connectors must knowcomponents in order to return result of asynchronous operations.17. Active RepositoryOverview– this pattern is a variation of Shared Repository that providesa notification mechanism to Repository. Client elements do not have toinvoke Repository to check if there is something meant for them. Instead,Repository can notify all registered ClientsElementsRepository – is a core element of the pattern. It is meant to store, maintaindata and provide it to clients.Client – uses repository to store data in it and to obtain data from it.Relationships – all the client elements are aware of the repository andcan perform operations on it. Since Repository can notify Clients, all theconnections between Clients and Repository are bidirectional18. Remote Procedure CallOverview – The pattern assumes that all the remote procedures shouldbe treated, as they were local. User should not know that a procedure is executedsomewhere in the network. The procedures are mainly provider–dependentand can change over the years, therefore the description of the elements andrelationships bellow refer to just an example implementation of the patternElementsClient– is a frontend of the application. This element allows user to perform
- Page 13 and 14: Chapter 1. Introduction 3technique
- Page 15 and 16: Chapter 1. Introduction 5was notice
- Page 17 and 18: Chapter 1. Introduction 7do not pro
- Page 19 and 20: Chapter 1. Introduction 9Chapter 4
- Page 21 and 22: Chapter 2. Related Work 11This chap
- Page 23 and 24: Chapter 2. Related Work 13(b) Chara
- Page 25 and 26: Chapter 2. Related Work 15Figure 2.
- Page 27 and 28: Chapter 2. Related Work 17Drawbacks
- Page 29 and 30: Chapter 2. Related Work 19Figure 2.
- Page 31 and 32: Chapter 2. Related Work 21Advantage
- Page 33 and 34: Chapter 2. Related Work 23between a
- Page 35 and 36: Chapter 2. Related Work 252. Applic
- Page 37 and 38: Chapter 2. Related Work 274. Mediat
- Page 39 and 40: Chapter 2. Related Work 292.3 Summa
- Page 41 and 42: Chapter 3. Architectural Patterns 3
- Page 43 and 44: Chapter 3. Architectural Patterns 3
- Page 45 and 46: Chapter 3. Architectural Patterns 3
- Page 47 and 48: Chapter 3. Architectural Patterns 3
- Page 49 and 50: Chapter 3. Architectural Patterns 3
- Page 51 and 52: Chapter 3. Architectural Patterns 4
- Page 53 and 54: Chapter 3. Architectural Patterns 4
- Page 55 and 56: Chapter 3. Architectural Patterns 4
- Page 57 and 58: Chapter 3. Architectural Patterns 4
- Page 59 and 60: Chapter 3. Architectural Patterns 4
- Page 61 and 62: Chapter 3. Architectural Patterns 5
- Page 63: Chapter 3. Architectural Patterns 5
- Page 67 and 68: Chapter 3. Architectural Patterns 5
- Page 69 and 70: Chapter 3. Architectural Patterns 5
- Page 71 and 72: Chapter 3. Architectural Patterns 6
- Page 73 and 74: Chapter 3. Architectural Patterns 6
- Page 75 and 76: Chapter 3. Architectural Patterns 6
- Page 77 and 78: Chapter 3. Architectural Patterns 6
- Page 79 and 80: Chapter 3. Architectural Patterns 6
- Page 81 and 82: Chapter 3. Architectural Patterns 7
- Page 83 and 84: Chapter 3. Architectural Patterns 7
- Page 85 and 86: Chapter 4. Service Oriented Archite
- Page 87 and 88: Chapter 4. Service Oriented Archite
- Page 89 and 90: Chapter 4. Service Oriented Archite
- Page 91 and 92: Chapter 4. Service Oriented Archite
- Page 93 and 94: Chapter 4. Service Oriented Archite
- Page 95 and 96: Chapter 4. Service Oriented Archite
- Page 97 and 98: Chapter 4. Service Oriented Archite
- Page 99 and 100: Chapter 4. Service Oriented Archite
- Page 101 and 102: Chapter 4. Service Oriented Archite
- Page 103 and 104: Chapter 4. Service Oriented Archite
- Page 105 and 106: Chapter 4. Service Oriented Archite
- Page 107 and 108: Chapter 4. Service Oriented Archite
- Page 109 and 110: Chapter 4. Service Oriented Archite
- Page 111 and 112: Chapter 4. Service Oriented Archite
- Page 113 and 114: Chapter 5. Guidelines 1035.1 Patter
Chapter 3. <strong>Architectural</strong> <strong>Pattern</strong>s 54Relationships – Client is a container for logic and Client Broker. Logic <strong>of</strong>the client can invoke the client broker but broker cannot invoke the logic.Supplier is a server proving requires operations. A supplier contains SupplierLogic and Supplier Broker. In opposite <strong>to</strong> Client, Broker invokes Logicand Logic cannot invoke Broker. The connection between Client and Supplieris bidirectional because an asynchronous connection is assumed. Theconnection can be also unidirectional, what removes connection from Supplier<strong>to</strong> Client (see figure 3.19).Client SupplierClient Logic Client Broker Supplier Broker Supplier LogicFigure 3.19: Example usage <strong>of</strong> Explicit Invocation pattern15. Peer —<strong>to</strong> —PeerOverview– the whole pattern consists <strong>of</strong> only one type <strong>of</strong> elements: peer.The pattern creates a network build with peers. The number <strong>of</strong> peers is notspecified because peers can join and leave the network dynamicallyElementsPeer – the whole network consists <strong>of</strong> only one type <strong>of</strong> element–Peer. Peer isa server and a client in the same time. This means that each “peer” requestsand consumes services. To start up each peer has <strong>to</strong> find at least one otherpeer <strong>to</strong> create a network. This problem can be solved by introducing fewdedicated public peers that are known <strong>to</strong> other peers.Relationships – there is no limitations in connections between peers (seefigure 3.20).16. C2Overview – this patter is another possible solution for system interactingwith users.ElementsComponent – contains logic <strong>of</strong> the systemConnec<strong>to</strong>r – forwards messages from one Component <strong>to</strong> another. Connectionsbetween Components and Connec<strong>to</strong>rs are asynchronous. Connec<strong>to</strong>rshave <strong>to</strong> be aware <strong>of</strong> all the Components “above” and “below” them.Relationships–All requests are asynchronous so the components have <strong>to</strong>know only components above in hierarchy <strong>to</strong> return the result. All requests