Optimization of a Biometric System Identification by Hand ... - SEE
Optimization of a Biometric System Identification by Hand ... - SEE
Optimization of a Biometric System Identification by Hand ... - SEE
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
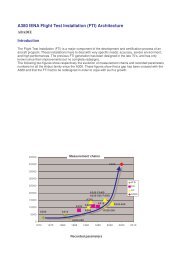
OPTIMIZATION OF A BIOMETRIC SYSTEM IDENTIFICATIONBY HAND GEOMETRYCarlos M. Travieso, Jesús B. Alonso, Sébastien David, Miguel A. FerrerDpto. de Señales y Comunicaciones, Universidad de Las Palmas de Gran CanariaCampus de Tafira, 35017 Las Palmas de Gran Canaria, SPAIN.Phone: +34 928 452 864 Fax: +34 928 451 243 email: ctravieso@dsc.ulpgc.esAbstractIn this paper the optimization <strong>of</strong> a very robust and novelsystem has been carried out to identify biometric <strong>by</strong> thehand geometry. Thus, a study between different type <strong>of</strong>geometric parameters like the distances betweenelements <strong>of</strong> the hand or the hand shape has been done.These parameters are used into two different types <strong>of</strong>classifiers, Neural Networks (NN) and Support VectorMachines (SVM). The best results have been foundusing the measures <strong>of</strong> distances in the hands, and whenSVM is used, achieving over a 99%, with at least threehands for the training in the identification system.It has been employed a supervised classificationsystem, utilizing therefore, two phases in the process <strong>of</strong>identification, one <strong>of</strong> training and another <strong>of</strong> test. For it,a database has been created with the particularity <strong>of</strong> alow resolution and a standard format.Key Words<strong>Biometric</strong>, <strong>Hand</strong> Recognition, Security <strong>System</strong>, SVM.1. IntroductionThe problem to resolve the identity <strong>of</strong> a person can beclassified fundamentally in two types <strong>of</strong> approaches [1]:recognition (more popularly known as identification)and verification. In this paper we focused on theidentification, which is based on determining theidentity <strong>of</strong> the subject inside a set <strong>of</strong> known identities.In many situations <strong>of</strong> our daily life, we are required totest our identity, as for example when we gain access toa precinct. A good recognition <strong>of</strong> the identity <strong>of</strong> aperson would be able to dissuade the delinquency andthe fraud, put new energy into the commercialtransactions and safeguards the critical resources.To approach the identification through a possessionhas the problem that this can be stolen, lost or forgotten,and falsified in the case <strong>of</strong> the cards with a magneticband. On the other hand, the problem <strong>of</strong> the use <strong>of</strong> theknowledge as identification form rests in the difficultyto re member the PINs. The PINs that are easilyremembered, it can be guessed for the swindler [2].Therefore, the use <strong>of</strong> the biometric will enable tosolve the problem <strong>of</strong> the personal identification. Thebiometric is easy to use, nothing to remember, nothingto change, nothing to lose. Besides, it provides a higherlevel <strong>of</strong> security, since it is somewhat univocal <strong>of</strong> acharacteristic human that can hardly be guessed ordeciphered. We work on the principle that somebiological characteristics are singular and unalterable,and besides , they are impossible to lose, to transfer or t<strong>of</strong>orget. This does them more dependable, friendly andsure than passwords [1].From all the possibilities <strong>of</strong> biometric parameters, ithas been chosen the hand, since it is a system very littlestudied with few references, [3][4][5][6][7], and peoplegive it credit as recognition system [1]. The use <strong>of</strong> thehand palm as measure <strong>of</strong> authentication can be a goodsolution for applications <strong>of</strong> intermediate security andwhere the convenience is considered as more importantoption than the security or the precision. At the sametime, this technique <strong>of</strong>fers a good balance betweenperformance and facility <strong>of</strong> use. The fast and easyintegration in others security systems does the use <strong>of</strong> thehand geometry an obvious first step for the industry inbiometric applications. In the following figure, it can beobserved as the biometric market is currently, where itsannual mean growth should be 31.5% between 2004and 2008 [8].The approach to problem <strong>of</strong> the identification carriedout up to now has been based on two premises:• A personal possession: in our case can be anidentification card or card <strong>of</strong> magnetic band.• The knowledge <strong>of</strong> information: as it can be a PIN(Personal <strong>Identification</strong> Number).Figure 1. 2004 Comparative Market Share <strong>by</strong> Technology [8]
Inside our system <strong>of</strong> biometric recognition, somesteps have already been made as the building <strong>of</strong> thedatabase and a first approximation with system basedon Neural Networks [7]. Therefore, in this paper, thefull study <strong>of</strong> classifier according to different parametersis presented. The scheme followed in this paper isshown in the figure 2. SVM has been selected likeclassifier because <strong>of</strong> the robust and good resultsprovided in [9][10]. In such a way, in this study, wetend to optimize the identification system.The rest <strong>of</strong> paper follows with the second section andthe description <strong>of</strong> the database. Subsequently, the imageprocessing applied for the extraction <strong>of</strong> characteristics.In the fourth section, the classification is described.Experiments are in the fifth section, and finally,conclusions.2. Building <strong>of</strong> the databaseWe will restrict the feature set mainly to the contour andto some geometrical measurements. We do not usepalm-print recognition (identification <strong>of</strong> a user based inthe information extracted from the lines <strong>of</strong> the palm).The quality <strong>of</strong> the images has been fixed to 150 dpi. T<strong>of</strong>acilitate further computation every scanned image hasbeen scaled <strong>by</strong> a factor <strong>of</strong> 20%. This scaling do notaffect the recognition rate, since all the images havebeen reduced <strong>by</strong> the same factor. The scaling processhas a two reasons:• We keep the image file size small.• The contour information is reduced making easierfurther processing.Table 1 summarizes the image databasecharacteristics.Properties <strong>of</strong> the images contained in the databaseSize80% <strong>of</strong> the original size.Quality150dpiColour256 grey levelsFile size1405K<strong>by</strong>tesMatrix size1403x1021Table 1. Images specificationsThe images have been obtained using 8 bitsresolution, which is the natural choice because <strong>of</strong> twomain reasons:• We do not need to save our image as coloured one,because no special feature as colour skin is used.• The scanner s<strong>of</strong>tware produces a very poor binaryconversion.Most <strong>of</strong> the users are within a selective age rangefrom 23 to 30 years old. Far away from simplicities, wehave selected the users to have approximately equalhand characteristics to see how the algorithms perform.The percent <strong>of</strong> males and females are not equal. In thedatabase, 68% <strong>of</strong> the users are males.The number <strong>of</strong> repetitions selected to elaborate thedatabase is based on the references [3], [4]. In [3], theauthors took 360 images belonging to 50 users(approximately 7 images per user). In [4], they took 20users and 10 images per user. In our work, the databaseis composed <strong>by</strong> 500 images (50 users and 10 repetitionsper user) taken from the users’ rigtht hand.3. Image processing: extraction <strong>of</strong>parametersOnce the database elaboration built, according to thescheme showed in the Figure 2, we should make a pre -processing <strong>of</strong> the data in order to simplify theparameterisation process. This stage can be split into thefollowing steps:• Binarization: the original images in our databaseare 256 grey level images. In this step, our goal isto convert the input 8-bit image into a binaryimage.• Contour and main points extraction: once the imagehas been binarized we proceed with the extraction<strong>of</strong> the principal points <strong>of</strong> the hand (geometryapproach) and <strong>of</strong> the hand-palm contour.• Computation <strong>of</strong> two significant parameters: thehand’s area and perimeter are computed.• Normalization <strong>of</strong> the hand contour: the contour <strong>of</strong>the hand is centred with respect to the centroid,hence achieving translation invariance.Acquisition<strong>of</strong> imagesPreprocessingExtraction <strong>of</strong>parametersClassificationTRAININGTESTTemplate<strong>Identification</strong>DecisionAcquisition<strong>of</strong> imagesPreprocessingExtraction <strong>of</strong>parametersFigure 2. <strong>Identification</strong> <strong>Biometric</strong> <strong>System</strong>
3.1. BinarizationAfter several experiments changing the threshold andplaying with different images extracted from thedatabase, we reach the conclusion that with a selectedbinarization threshold <strong>of</strong> 65 the results were adequatefor our purposes. We tried other binarization algorithmas the suggested <strong>by</strong> Lloyd, Ridler-Calvar and Otsu[11][12]. The two first algorithms gave us a threshold <strong>of</strong>100 and the third one a threshold <strong>of</strong> 185. The last valuewas completely discarded, since the output imageapplying this threshold <strong>of</strong> 185 is worse than the case“High Threshold” showed in the Figure 3. For a value<strong>of</strong> 100 there were not so many differences since smallvariations in the threshold will not affect the finalresults.To complete precisely the hand-palm geometry thereare still three important points missing. These points arethe symmetric to the points located in the little-ringfinger valley, index-ring finger valley and index-thumbvalley. We can see the positions <strong>of</strong> these points inFigure 5, pointed <strong>by</strong> the labels (X1, Y1), (X2, Y2) and(X3, Y3), respectively. To locate these points we haveto look for the outer points in the contour withminimum distance to these valleys.Finally, using all the main points previouslycomputed, the geometric measurements are obtained.We take the following distances: Length <strong>of</strong> the 5fingers, distances between points (X1, Y1) and(X2,Y2), points (X2,Y2) and the valley between thethumb and index finger and the points (X3,Y3) and(X1,Y1). Figure 5 shows the final results along with thegeometric measurements taken into account.(a) Low (b) High (c) SelectedFigure 3 Different thresholds applied to the sample image3.2. Contour and main points extractionOnce the images have been binarized we have to extractthe most significant data mentioned above. Featureextraction is a very important step in building ourbiometric identification system because a wrong featureselection provides low recognition rates. In this paperwe have used two parameters, hand contour andgeometric measuments.The contour is calculated from the binarizated image<strong>by</strong> the derivate. As one <strong>of</strong> our objectives is to recognizeusers <strong>by</strong> the hand contour, we need to obtain anumerical sequence describing the hand-palm shape.Contour following is a procedure <strong>by</strong> which we runthrough the hand silhouette <strong>by</strong> following the image’sedge. In our implementation, we take into account theradius from gravedad center to hand shape. Figure 4shows this process and the vector <strong>of</strong> parametersimplemented with boundary codification.ContourCodificationFigure 4. Contour and its parametersThe method for extraction the geometric hand-palmfeatures is quite straightforward. The first points to bedetected are the thumb and the little finger. By thesetwo points, we are able to extract most <strong>of</strong> thegeometrical information. With those two points , welocate the following main points: finger tips, valleysbetween the fingers.Figure 5. Contour and geometric measurements3.3. Computation <strong>of</strong> two significant parametersThose parameters are the area and the perimeter,calculated with the binarizated and contour images,respectively.3.4. Normalization <strong>of</strong> the hand contourThe contour vectors characterizing the silhouette <strong>of</strong>each hand-palm are quite large in length (about 4000samples). We should reduce these lengths as much aswe can, preserving the information needed for theclassification. The techniques used in this paper toextract and compress the information presented in acontour parameter vector are transformed descriptors[12][13] and Principal Component Analysis (PCA) [14].• Discrete Cosine Transform Descriptors [12]: it hasexcellent energy compaction for highly correlateddata. The DCT basis images are independent inputsand its information packing ability is close to theoptimal KLT. The DCT <strong>of</strong> a sequence is definedu( n),0 ≤ n ≤ N −1as:{ }N 1⎡ (2 + 1) ⎤( ) = ( ) ∑ − π n kv k α k u(n)cos⎢,0 ⎣ 2 ⎥n=N ⎦0 ≤ k ≤ N −1(1)
where12α( 0) = , α(k)= for 1 ≤ k ≤ N −1.NN(2)Signal restoration is possible <strong>by</strong> applying theinverse transform given <strong>by</strong>N 1⎡ (2 + 1) ⎤( ) = ∑ − π nu n α(k ) v(k ) cos⎢,0⎣ 2 ⎥k =N ⎦0 ≤ n ≤ N −1.(3)Choosing the appropriate v(k) coefficients we get agood reduction in the number <strong>of</strong> coefficients whilekeeping as much information as possible.• Discrete Wavelets Transform Descriptors [13]:discrete orthogonal wavelet transform is used todecompose a signal into several levels <strong>of</strong>resolution. Multiresolution decomposition isperformed <strong>by</strong> projecting the signal onto orthogonalapproximation and detail subspaces. An efficientway <strong>of</strong> implementing discrete wavelet transform(DWT) is the use <strong>of</strong> filter banks. The filter bankimplementation <strong>of</strong> DWT is based on itsmultiresolution property.• Principal Comp onent Analysis [14]: PCA alsoknown as the Karhunen-Loève transform, can beused to reduce the feature vector dimension whileretaining the feature information <strong>by</strong> constructing alinear transformation matrix. The transformationmatrix is made up <strong>of</strong> the most significanteigenvectors <strong>of</strong> the feature vector covariancematrix. The eigenvectors are orthonormal(orthogonal and normalized) so they transform theoriginal data into independent feature informationhaving maximal variance.Finally, once the useful data has been extracted fromthe images, we store the new parameters. The geometricmeasurements is a structure that contains the 10geometric measurements extracted from the hand (5finger lengths, 3 ratio measurements, area & perimeter).On the other hand, we have to notice that the length <strong>of</strong>the contour parameters for each user is quite long. Forthis reason, we reduce with above techniques in size <strong>of</strong>128, 256 and 512 samples.two different classes. This decision boundary orseparate hyperplane can be designed with differentkernels, lineal, polynomial, gaussian, etc.Supposing that all the data <strong>of</strong> training satisfy thefollowing conditions:x i· w + b ≥ +1x i· w + b ≤ −1for y i = +1 (4)for y i = +1 (5)These two conditions can be transformed in a set <strong>of</strong>inequations:yi( x · w + b) −1≥ 0ifor ∀i(6)It is observed that the points which comply with theequality <strong>of</strong> the equation 4, they are found in thehyperplane H 1 : x i· w + b = 1 with normal w and distanceperpendicular since the origin1− b.wSimilarly, the contained points in the equality <strong>of</strong> theequation 5 are found in the hyperplane H 2 :xi· w + b = −1 with normal w and distance perpendicularsince the origin −1 − b .wThe distances between H 1 and H 2 will be equal to 1 .For which the margin will be 2 .wwThe above H1 and H2 are parallels (have the samenormal) and no point <strong>of</strong> the training is located betweenthem. It will be able to find the pair <strong>of</strong> hyperplanes that2they give the most maximum margin minimizing w ,subject to the conditions <strong>of</strong> the equation 6.Therefore the solution <strong>of</strong> a typical two-dimensionalcase would have the following form:4. ClassificationTo carry out the study have been utilized two classifiersto observe the adaptation <strong>of</strong> the data to different robustforms to classify geometric parameters. Theseclassifiers are Support Vector Machines (SVM)[15][16] and Neural Networks (NN) [14][17].4.1. Support Vector MachinesSupport Vector− bwH 2HH 1wThe Support Vector Machines (SVM) resolve theclassification <strong>of</strong> geometric parameters to calculateexactly the separate hyperplane from the training data[15][16]. Besides, this solution introduces methods tobe able to work with no separable and separable lineallycases <strong>of</strong> the data. The decision boundary is decided withthe calculation <strong>of</strong> a separate hyperplane thatdiscriminates between the positive and the negativesamples; therefore a SVM treats the classification asFigure 6. Separate lineal hyperplanemarginFor the identification system in this paper, a SVM withkernel lineal and RBF has been used, as not linealseparate plane. As the samples are separated in groups<strong>of</strong> two classes, we have established a multiple classesstructure for the 50 different hands.
4.2. Neural NetworksThe perceptron <strong>of</strong> a simple layer establishes itscorrespondence with a rule <strong>of</strong> discrimination betweenclasses based on discriminante lineal. However, it ispossible to define discriminations for not lineallyseparable classes utilizing multilayer perceptrons, thatare networks without refreshing (feed-forward) with oneor more layers <strong>of</strong> nodes between the input layer and exitlayer. These additional layers contain hidden neurons ornodes, which are directly connected to the input andoutput layer [14][17]. A neural network multilayerperceptron (NN-MLP) <strong>of</strong> three layers is shown in thefigure 7, with two layers <strong>of</strong> hidden neurals . Each neuronis associated with a weight and a bias, these weights anbiases <strong>of</strong> the connections <strong>of</strong> the network will be trainedto make their values suitable for the classificationbetween the different classes.Output layer2º hiddenlayer1º hiddenlayerInput layerFigure 7. Multilayer PerceptronParticularly, the neural network used in theexperiments is a Multilayer Perceptron (MLP) Feed-Forward with Back-Propagation training algorithm, andwith only one hidden layer.5. ExperimentsThe experiments have been based on the use <strong>of</strong> thedifferent parameters, for the two classifiers proposed.Therefore, the first step is to seek the optimum values <strong>of</strong>the classifier for each one <strong>of</strong> the parameters (theseresults are not shown for limitations <strong>of</strong> space in thispaper).The combinations studied for the different classifiersare;• Geometric Measures (GM-10)• Contour with DCT reduction to 128• Contour with DCT reduction to 256• Contour with DCT reduction to 512• Contour with DWT reduction to 128• Contour with DWT reduction to 256• Contour with DWT reduction to 512• Contour with PCA reduction to PCA 128The results obtained for each one <strong>of</strong> the classifierswith the optimized variables, can be observed in thefollowing tables;Maximum Recognition RateNumbers <strong>of</strong> hands 3 5 7 9DCT-128 92.21% 96.20% 98.00% 99.00%DWT-128 92.11% 96,92% 98,4% 98,8%PCA-128 84.02% 92.92% 94,66% 96,2%GM -10 99.02% 99.56% 99.73% 99.8%Table 2. Results with NNThese better results have been found for 58 neuronsin the hidden layer. From the above table 2, it can bededuced that the best parameters are the geometricmeasures, surpassing always the 99% <strong>of</strong> success as thenumber <strong>of</strong> hands for training, and the worst one <strong>by</strong> thereduction with PCA. With the transformed descriptorsparameters, the results are low in comp arison withgeometrical measurement (GM -10). Finally, it iscommented that the results obtained are the best rates <strong>of</strong>peak that were registered, due to that the neuralnetworks vary quite a lot, their recognition rate sincethey are randomly started.For the pro<strong>of</strong>s carried out with SVM, the experimentswith PCA have been ruled out, since they have obtainedthe worst success. Thus, we focus on the tests with thetransformed descriptors and geometrical measures. Theresults are shown in the following table, where variablesare the different types <strong>of</strong> parameters and the type <strong>of</strong>kernel <strong>of</strong> the SVM. The recognition rates have beencalculated with the optimized SVM for the lineal andRBF kernel.Mean Recognition RateNumbers <strong>of</strong> hands 4 5 6DCT-128lineal 92.27% 93.36% 94.60%RBF 85.17% 86.89% 89.00%DCT-256lineal 92.53% 93.92% 95.00%RBF 85.75% 87.21% 89.50%DCT-512lineal 92.73% 93.71% 95.50%RBF 83.25% 86.78% 91.12%DWT-128lineal 92.10% 93.45% 94.78%RBF 80.54% 84.61% 87.39%DWT-256lineal 92.67% 93.92% 95.10%RBF 82.53% 87.68% 89.37%DWT-512lineal 92.00% 94.72% 95.10%RBF 80.93% 86.08% 88.20%GM-10lineal 86.67% 89.44% 88.70%RBF 99.67% 99.84% 99.90%Table 3. Results with SVMIn the table 3, the experiments have been made with4, 5 and 6 training hands. Moreover, from the abovetables, we can deduce that the NN-MLP and the SVMwith kernel lineal have the same response fordescriptors transformed. On the other hand, the SVMwith kernel RBF responds better than the NN in the use<strong>of</strong> geometric measures. This is due to that the NN startthe training with a random beginning, move the
decision boundary until all the points <strong>of</strong> training are inthe correct side <strong>of</strong> the decision. Nevertheless, theSVM’s calculate its margin <strong>of</strong> more optimum form,between the support vector <strong>of</strong> each class, obtaining themean line (decision boundary) <strong>of</strong> both lines.Thinking about those better results, and in a possiblecommercial application, the following table shows therates averaged <strong>of</strong> the best case in this study and theirtypical deviation, after being carried out the experimentin 5 times, emphasizing the case <strong>of</strong> the training with 3hands, that <strong>of</strong> each 1000 hands is mistaken in 2.3 withtypical deviation <strong>of</strong> 0.13;NumbersMeanStandard<strong>of</strong> handsdeviation1 97.29% 1.052 99.10% 0.453 99.77% 0.134 99.67% 05 99.84% 0.226 99.90% 0.22Table 4. Best results with GM-10 and SVM with kernel RBF.6. ConclusionsA biometric identification system has been created <strong>by</strong>the hand geometry, which is very robust and with goodresults, upper 99%, using geometric measures andclassifying them with SVM.It has been shown thanks to this study that the use <strong>of</strong>the SVM with the same parameters than the NN andwith an adequate training improves the efficiency <strong>of</strong> thisidentification biometric system.The next step is to increase the hand database, and tostudy if these good results remain similar.The good results indicate that this biometric systemcan be integrated for commercial applications <strong>of</strong> accessto precincts, control <strong>of</strong> timetables, etc., since turns outto be efficient and the times <strong>of</strong> test are lower to onesecond.8. Acknowledgement[4] R. Sanchez-Reillo, <strong>Hand</strong> geometry patternrecognition through Gaussian mixture modelling,Proc. 15th International Conf. on PatternRecognition, Barcelona, Spain, vol. 2, 2000, 937-940.[5] A.K. Jian & N. Duta, Deformable matching <strong>of</strong>hand shapes for user verification, Proc. 15thInternational Conf. on Pattern Recognition,Barcelona, Spain, vol. 2, 1999, 857 -861.[6] Dong-mei Sun, Zheng-ding Qiu & Bing He,Automated identity verification based on handshapes, Proc. 6th International Conf. on SignalProcessing, vol. 2, 2002, 1596 -1599.[7] S. González, C.M. Travieso, J.B. Alonso & M.A.Ferrer, Automatic <strong>Biometric</strong> <strong>Identification</strong> system<strong>by</strong> hand geometry, Proc. 37th IEEE InternationalCarnahan Conf. on Security Technology, Taipei,Taiwan, 2003, 39-42.[8] <strong>Biometric</strong>s Market Report 2003-2007. Visited inFebruary 2004. [www.biometricgroup.com].[9] T. Joachims, Learning to classify text usingsupport vector machines (Kluwer AcademicPublishers, 2001).[10] C.M. Travieso, J.B. Alonso & M.A. Ferrer, SignLanguage to text <strong>by</strong> SVM, Proc. 7th InternationalSymposium on Signal Processing and itsApplications, Paris, France, vol. 2, 2003, 439-442.[11] L. O’Gorman & R. Kasturi, Document ImageAnalysis (IEEE Computer Society Press, 1995).[12] Anil K. Jain, Fundamentals <strong>of</strong> Digital ImageProcessing. (Prentice Hall. 1989).[13] A. Graps, An introduction to wavelets ,IEEE Computational Science and Engineering,2(2),1995, 50-61.[14] C. M. Bishop, Neural Networks for PatternRecognition (Oxford University Press, 1995).[15] N. Cristianini & J. Shawe-Taylor, An introductionto support vector machines (Cambridge UniversityPress, Cambridge, 2000).[16] B. Schöfkopf, C. Burges & A. Smola, PairwiseClassification and Support Vector Machines (TheMIT Press, Cambridge, Massachusetts, London,England, 1999).[17] D.R. Hush & B.G. Horne, Progress in supervisedneural networks, IEEE Signal ProcessingMagazine, 10(1), 1993, 8-39.This work has been developed and agrees <strong>by</strong> researchProject UNI2003/26 from University <strong>of</strong> Las Palmas deGran Canaria (Spain).References[1] A.K. Jain, R. Bolle, & S. Pankanti, <strong>Biometric</strong>s:Personal <strong>Identification</strong> (Networked Society,Kluwer Academic Publishers, 2001).[2] J. R. Parks, Personal identification – biometrics(North Holland: Elsevier Science, 1991).[3] A.K. Jain, A. Ross & S. Pankanti, A prototypehand geometry-based verification system, Proc.2nd International Conf. on Audio and Video based<strong>Biometric</strong> Person Authentication, 1999, 166-171.