dynamic signature verification with template protection using ... - ATVS
dynamic signature verification with template protection using ... - ATVS
dynamic signature verification with template protection using ... - ATVS
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
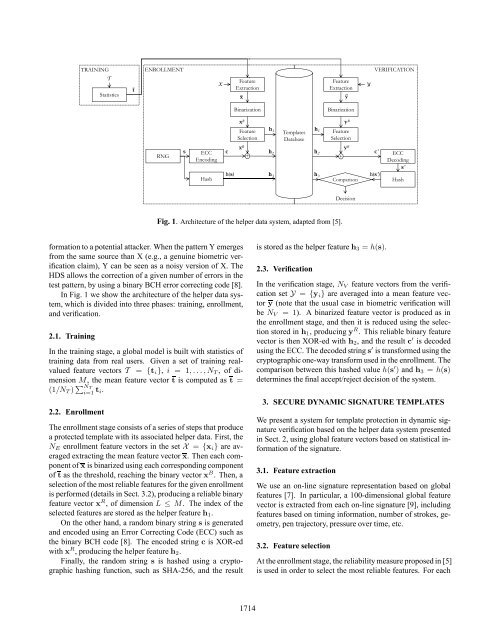
Fig. 1. Architecture of the helper data system, adapted from [5].formation to a potential attacker. When the pattern Y emergesfrom the same source than X (e.g., a genuine biometric vericationclaim), Y can be seen as a noisy version of X. TheHDS allows the correction of a given number of errors in thetest pattern, by <strong>using</strong> a binary BCH error correcting code [8].In Fig. 1 we show the architecture of the helper data system,which is divided into three phases: training, enrollment,and verication.2.1. TrainingIn the training stage, a global model is built <strong>with</strong> statistics oftraining data from real users. Given a set of training realvaluedfeature vectors T = {t i }, i = 1,...,N T ,ofdimensionM, the mean feature vector t is computed as t =(1/N T ) ∑ N Ti=1 t i.2.2. EnrollmentThe enrollment stage consists of a series of steps that producea protected <strong>template</strong> <strong>with</strong> its associated helper data. First, theN E enrollment feature vectors in the set X = {x i } are averagedextracting the mean feature vector x. Then each componentof x is binarized <strong>using</strong> each corresponding componentof t as the threshold, reaching the binary vector x B . Then, aselection of the most reliable features for the given enrollmentis performed (details in Sect. 3.2), producing a reliable binaryfeature vector x R ,ofdimensionL ≤ M. The index of theselected features are stored as the helper feature h 1 .On the other hand, a random binary string s is generatedand encoded <strong>using</strong> an Error Correcting Code (ECC) such asthe binary BCH code [8]. The encoded string c is XOR-ed<strong>with</strong> x R , producing the helper feature h 2 .Finally, the random string s is hashed <strong>using</strong> a cryptographichashing function, such as SHA-256, and the resultis stored as the helper feature h 3 = h(s).2.3. VericationIn the verication stage, N V feature vectors from the vericationset Y = {y i } are averaged into a mean feature vectory (note that the usual case in biometric verication willbe N V =1). A binarized feature vector is produced as inthe enrollment stage, and then it is reduced <strong>using</strong> the selectionstored in h 1 , producing y R . This reliable binary featurevector is then XOR-ed <strong>with</strong> h 2 , and the result c ′ is decoded<strong>using</strong> the ECC. The decoded string s ′ is transformed <strong>using</strong> thecryptographic one-way transform used in the enrollment. Thecomparison between this hashed value h(s ′ ) and h 3 = h(s)determines the nal accept/reject decision of the system.3. SECURE DYNAMIC SIGNATURE TEMPLATESWe present a system for <strong>template</strong> <strong>protection</strong> in <strong>dynamic</strong> <strong>signature</strong>verication based on the helper data system presentedin Sect. 2, <strong>using</strong> global feature vectors based on statistical informationof the <strong>signature</strong>.3.1. Feature extractionWe use an on-line <strong>signature</strong> representation based on globalfeatures [7]. In particular, a 100-dimensional global featurevector is extracted from each on-line <strong>signature</strong> [9], includingfeatures based on timing information, number of strokes, geometry,pen trajectory, pressure over time, etc.3.2. Feature selectionAt the enrollment stage, the reliability measure proposed in [5]is used in order to select the most reliable features. For each1714