Administrator's Guide - Kerio Software Archive
Administrator's Guide - Kerio Software Archive Administrator's Guide - Kerio Software Archive
Chapter 7 DomainsUsernameName of the user that have read rights for the LDAP database, either of the root useror of the Open Directory administrator (admin for Mac OS X 10.3 or diradmin for MacOS X 10.4). In case that the administrator’s username is used, it is necessary to makesure the user is an OpenDirectory Administrator, not just a local administrator on theOpenDirectory computer.To connect to the Apple OpenDirectory database insert an appropriate username in thefollowing form:uid=xxx,cn=xxx,dc=xxx• uid — username that you use to connect to the system.• cn — name of the users container (typically the users file).• dc — names of the domain and of all its subdomains (i.e. mail.company.com →dc=mail1,dc=company,dc=com)PasswordPassword of the user that have read rights for the LDAP database.Secured connection (LDAPS)Within the communication of the LDAP database with Kerio MailServer, sensitive datamay be transmitted (such as user passwords). It is possible to secure the communicationby using an SSL tunnel.Warning: SSL encryption is demanding in respect of connection speed and processor operation.Especially when too many connection are established between the LDAP databaseand Kerio MailServer or when too many users are included in the LDAP database, the communicationmight get slow. If the SSL encryption overloads the server, it is recommendedto use the non-secured version of LDAP.Domain controller failoverDNS name or IP address of the backup server with the same LDAP database.Note: If the secured version of LDAP service is used for connection, it is necessary toenter also the DNS name to enable the SSL certificate’s verification.LDAP search suffixIf the Apple OpenDirectory option is selected in the Directory service type entry, inserta suffix in the following form: dc=subdomain,dc=domain.Click the Test connection button to check the defined parameters. The test is performed onthe server name and address (if it is possible to establish a connection with the server) as wellas the username and password (if authentication can be performed).Note: Cooperation with the LDAP database that has been described above has nothing to dowith the built-in LDAP server. The built-in LDAP server is used to access contact lists frommail clients (for details refer to the chapter 19). However, if the MailServer is installed onan Apple Open Directory server the LDAP listening port in the MailServer’s Configuration →Services must be changed to an alternate port to avoid a port conflict.74
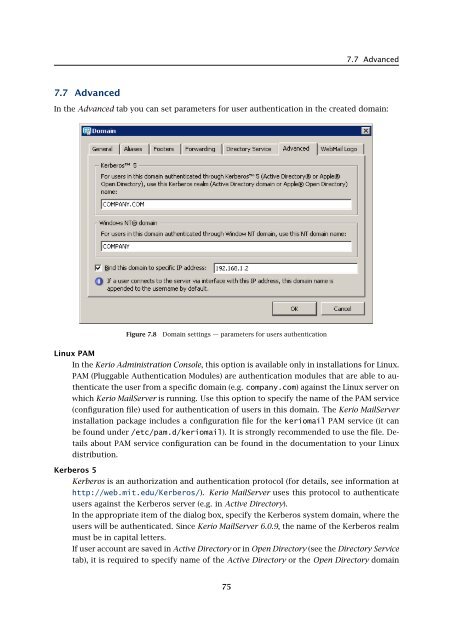
7.7 Advanced7.7 AdvancedIn the Advanced tab you can set parameters for user authentication in the created domain:Figure 7.8Domain settings — parameters for users authenticationLinux PAMIn the Kerio Administration Console, this option is available only in installations for Linux.PAM (Pluggable Authentication Modules) are authentication modules that are able to authenticatethe user from a specific domain (e.g. company.com) against the Linux server onwhich Kerio MailServer is running. Use this option to specify the name of the PAM service(configuration file) used for authentication of users in this domain. The Kerio MailServerinstallation package includes a configuration file for the keriomail PAM service (it canbe found under /etc/pam.d/keriomail). It is strongly recommended to use the file. Detailsabout PAM service configuration can be found in the documentation to your Linuxdistribution.Kerberos 5Kerberos is an authorization and authentication protocol (for details, see information athttp://web.mit.edu/Kerberos/). Kerio MailServer uses this protocol to authenticateusers against the Kerberos server (e.g. in Active Directory).In the appropriate item of the dialog box, specify the Kerberos system domain, where theusers will be authenticated. Since Kerio MailServer 6.0.9, the name of the Kerberos realmmust be in capital letters.If user account are saved in Active Directory or in Open Directory (see the Directory Servicetab), it is required to specify name of the Active Directory or the Open Directory domain75
- Page 23 and 24: 2.4 InstallationFigure 2.5Custom in
- Page 25 and 26: 2.4 InstallationKerio MailServer En
- Page 27 and 28: 2.4 InstallationThe product support
- Page 29 and 30: 2.4 Installation(Kerio Administrati
- Page 31 and 32: 2.5 Configuration WizardNote: The c
- Page 33 and 34: 2.5 Configuration WizardFigure 2.16
- Page 35 and 36: 2.6 Upgrade and UninstallationWhen
- Page 37 and 38: Chapter 3Product Registration and L
- Page 39 and 40: 3.2 Registration with the administr
- Page 41 and 42: 3.2 Registration with the administr
- Page 43 and 44: 3.3 License information and import
- Page 45 and 46: 3.4 Licensing policyOnce number of
- Page 47 and 48: 4.1 Kerio MailServer MonitorFigure
- Page 49 and 50: 4.2 Standalone processes of the ser
- Page 51 and 52: 5.2 Administration WindowThe same d
- Page 53 and 54: 5.2 Administration WindowStatus bar
- Page 55 and 56: Chapter 6ServicesIn Configuration
- Page 57 and 58: 6.1 Service Parameter Settings• a
- Page 59 and 60: 6.1 Service Parameter SettingsFigur
- Page 61 and 62: 6.3 TroubleshootingFigure 6.5The De
- Page 63 and 64: Chapter 7DomainsKerio MailServer ca
- Page 65 and 66: 7.2 GeneralFigure 7.2Domain setting
- Page 67 and 68: 7.4 FootersFigure 7.3Domain setting
- Page 69 and 70: 7.5 ForwardingFigure 7.5Domain sett
- Page 71 and 72: 7.6 Setting of Directory ServicesFi
- Page 73: 7.6 Setting of Directory ServicesFi
- Page 77 and 78: 7.8 WebMail Logo3. In the Logging m
- Page 79 and 80: 8.2 Sending High Priority MessagesW
- Page 81 and 82: Chapter 9SchedulingKerio MailServer
- Page 83 and 84: 9.2 Optimal Scheduling9.2 Optimal S
- Page 85 and 86: 10.1 Kerio MailServer CertificateFi
- Page 87 and 88: 10.1 Kerio MailServer Certificate
- Page 89 and 90: 10.2 Install certificates on client
- Page 91 and 92: 10.2 Install certificates on client
- Page 93 and 94: 10.2 Install certificates on client
- Page 95 and 96: 11.3 LanguageIf there is one of the
- Page 97 and 98: 11.3 LanguageFigure 11.1Dictionary
- Page 99 and 100: 12.2 Time IntervalsClick on Add to
- Page 101 and 102: 12.3 Setting Remote AdministrationF
- Page 103 and 104: 10312.3 Setting Remote Administrati
- Page 105 and 106: 13.2 Creating a user accountWarning
- Page 107 and 108: 13.2 Creating a user accountFigure
- Page 109 and 110: 13.2 Creating a user accountStore p
- Page 111 and 112: 13.2 Creating a user accountNote: T
- Page 113 and 114: 13.2 Creating a user accountFigure
- Page 115 and 116: 13.3 Editing User AccountNote: When
- Page 117 and 118: 13.5 Removing user accountsKerio Ma
- Page 119 and 120: 13.9 Administration of mobile devic
- Page 121 and 122: 13.9 Administration of mobile devic
- Page 123 and 124: 13.10 Import Users• MailAddress
7.7 Advanced7.7 AdvancedIn the Advanced tab you can set parameters for user authentication in the created domain:Figure 7.8Domain settings — parameters for users authenticationLinux PAMIn the <strong>Kerio</strong> Administration Console, this option is available only in installations for Linux.PAM (Pluggable Authentication Modules) are authentication modules that are able to authenticatethe user from a specific domain (e.g. company.com) against the Linux server onwhich <strong>Kerio</strong> MailServer is running. Use this option to specify the name of the PAM service(configuration file) used for authentication of users in this domain. The <strong>Kerio</strong> MailServerinstallation package includes a configuration file for the keriomail PAM service (it canbe found under /etc/pam.d/keriomail). It is strongly recommended to use the file. Detailsabout PAM service configuration can be found in the documentation to your Linuxdistribution.Kerberos 5Kerberos is an authorization and authentication protocol (for details, see information athttp://web.mit.edu/Kerberos/). <strong>Kerio</strong> MailServer uses this protocol to authenticateusers against the Kerberos server (e.g. in Active Directory).In the appropriate item of the dialog box, specify the Kerberos system domain, where theusers will be authenticated. Since <strong>Kerio</strong> MailServer 6.0.9, the name of the Kerberos realmmust be in capital letters.If user account are saved in Active Directory or in Open Directory (see the Directory Servicetab), it is required to specify name of the Active Directory or the Open Directory domain75