Administrator's Guide - Kerio Software Archive
Administrator's Guide - Kerio Software Archive Administrator's Guide - Kerio Software Archive
Chapter 15 Sending and Receiving MailSSL traffic must be allowed to all protocols at all client stations. The secured connectionis set automatically upon a successful connection to Kerio WebMail.The only exception from this restriction is the SMTP protocol. Due to the plenty of SMTPservers which do not support SMTPS and STARTTLS, it is not possible to allow the secureversion of the protocol only. To still provide sufficient security, the SMTP server requiressecure password authentication for the SMTP protocol upon enabling the Require encryptedconnection option. Name and password are still sent by one of the supportedsecure authentication methods.After the security policy is defined, you can create an exception for a group of IP addressesfor which the secured connection will not be required. For this purpose, eithera new IP group can be created or an existing one can be selected. For information on IPaddress settings, see chapter 12.1.If you decide for this communication protection method, make sure that all users havea valid authentication certificate installed on their client stations (for more information,see chapter 10).Supported authentication methodsKerio MailServer supports the following methods of user authentication:Figure 15.18Authentication methods• CRAM-MD5 — password authentication method (using MD5 digests). This method is quitecommon and many email clients provide support for it.• DIGEST-MD5 — password authentication method (using MD5 digests).• LOGIN — user passwords are completely unprotected during transfer. If this method isused, it is strongly recommended to enable SSL tunnel connection.• NTLM — this method can be used only in case users are authenticated against an ActiveDirectory domain. It is applicable only to the user accounts that were imported from ActiveDirectory. Configuration of NTLM authentication is addressed in chapter 25.• PLAIN — user passwords are completely unprotected during transfer. If this method isused, it is strongly recommended to enable SSL tunnel connection.• APOP — the authentication method is not displayed in the list, Kerio MailServer uses itautomatically to download POP3 accounts.The server provides all the above mentioned authentication methods. They are ordered thesame way as in the table below (from CRAM-MD5). If the selected method is supported by theclient, the other methods will not be used. However, a problem may occur if the passwordis stored in the secure format (SHA1). If this encryption method is used, only LOGIN and160
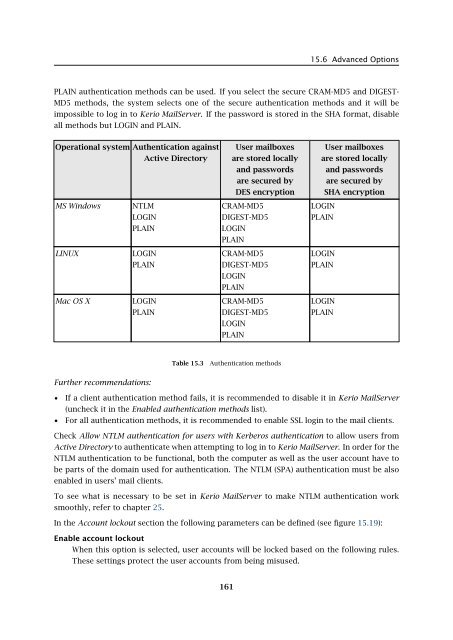
15.6 Advanced OptionsPLAIN authentication methods can be used. If you select the secure CRAM-MD5 and DIGEST-MD5 methods, the system selects one of the secure authentication methods and it will beimpossible to log in to Kerio MailServer. If the password is stored in the SHA format, disableall methods but LOGIN and PLAIN.Operational system Authentication againstActive DirectoryUser mailboxesare stored locallyand passwordsare secured byDES encryptionUser mailboxesare stored locallyand passwordsare secured bySHA encryptionMS WindowsNTLMCRAM-MD5LOGINLOGINDIGEST-MD5PLAINPLAINLOGINPLAINLINUXLOGINCRAM-MD5LOGINPLAINDIGEST-MD5PLAINLOGINPLAINMac OS XLOGINCRAM-MD5LOGINPLAINDIGEST-MD5PLAINLOGINPLAINTable 15.3Authentication methodsFurther recommendations:• If a client authentication method fails, it is recommended to disable it in Kerio MailServer(uncheck it in the Enabled authentication methods list).• For all authentication methods, it is recommended to enable SSL login to the mail clients.Check Allow NTLM authentication for users with Kerberos authentication to allow users fromActive Directory to authenticate when attempting to log in to Kerio MailServer. In order for theNTLM authentication to be functional, both the computer as well as the user account have tobe parts of the domain used for authentication. The NTLM (SPA) authentication must be alsoenabled in users’ mail clients.To see what is necessary to be set in Kerio MailServer to make NTLM authentication worksmoothly, refer to chapter 25.In the Account lockout section the following parameters can be defined (see figure 15.19):Enable account lockoutWhen this option is selected, user accounts will be locked based on the following rules.These settings protect the user accounts from being misused.161
- Page 109 and 110: 13.2 Creating a user accountStore p
- Page 111 and 112: 13.2 Creating a user accountNote: T
- Page 113 and 114: 13.2 Creating a user accountFigure
- Page 115 and 116: 13.3 Editing User AccountNote: When
- Page 117 and 118: 13.5 Removing user accountsKerio Ma
- Page 119 and 120: 13.9 Administration of mobile devic
- Page 121 and 122: 13.9 Administration of mobile devic
- Page 123 and 124: 13.10 Import Users• MailAddress
- Page 125 and 126: 13.10 Import UsersFor detailed info
- Page 127 and 128: 13.10 Import UsersFigure 13.24Impor
- Page 129 and 130: 13.12 User Account TemplatesNote: C
- Page 131 and 132: Chapter 14User groupsUser accounts
- Page 133 and 134: 14.1 Creating a User GroupGroup add
- Page 135 and 136: 14.1 Creating a User GroupPublish t
- Page 137 and 138: 15.1 Mail Delivery over the Interne
- Page 139 and 140: 15.1 Mail Delivery over the Interne
- Page 141 and 142: 15.2 SMTP serverinterface originall
- Page 143 and 144: 15.2 SMTP serverAuthentication by I
- Page 145 and 146: 15.2 SMTP serverLimit maximum incom
- Page 147 and 148: 15.3 AliasesMaximum number of deliv
- Page 149 and 150: 15.3 AliasesCharacter typea-zA-ZDes
- Page 151 and 152: 15.4 remote POP3 mailboxesFigure 15
- Page 153 and 154: 15.4 remote POP3 mailboxesthe messa
- Page 155 and 156: 15.4 remote POP3 mailboxesFigure 15
- Page 157 and 158: 15.6 Advanced OptionsDescriptionA c
- Page 159: 15.6 Advanced Optionsnot have to wo
- Page 163 and 164: 15.6 Advanced OptionsWatchdog Hard
- Page 165 and 166: 15.6 Advanced OptionsFigure 15.22HT
- Page 167 and 168: 15.6 Advanced Optionsstartup of the
- Page 169 and 170: 15.6 Advanced OptionsKerio WebMail
- Page 171 and 172: 16.1 Spam Rating tab16.1 Spam Ratin
- Page 173 and 174: 16.2 Blacklists tabtration Console
- Page 175 and 176: 16.2 Blacklists tabInternet databas
- Page 177 and 178: 16.3 Custom RulesSORBSSpam and Open
- Page 179 and 180: 16.3 Custom RulesUse the Add button
- Page 181 and 182: 16.3 Custom RulesTypeType of condit
- Page 183 and 184: 16.4 SpamAssassinFigure 16.7SpamAss
- Page 185 and 186: 16.5 Email policy records checksend
- Page 187 and 188: 16.6 Spam repellentFigure 16.9SPFOn
- Page 189 and 190: 16.7 Recommended configuration of a
- Page 191 and 192: 16.7 Recommended configuration of a
- Page 193 and 194: 16.8 Monitoring of spam filter’s
- Page 195 and 196: 16.8 Monitoring of spam filter’s
- Page 197 and 198: 17.1 Integrated McAfee Anti-VirusBe
- Page 199 and 200: 17.4 Server responses to detection
- Page 201 and 202: 17.5 Filtering Email Attachments17.
- Page 203 and 204: 17.6 Antivirus control statisticsFi
- Page 205 and 206: 18.1 ArchivingPath to the archive d
- Page 207 and 208: 18.2 Backup of user foldersFigure 1
- Page 209 and 210: 18.2 Backup of user foldersFigure 1
15.6 Advanced OptionsPLAIN authentication methods can be used. If you select the secure CRAM-MD5 and DIGEST-MD5 methods, the system selects one of the secure authentication methods and it will beimpossible to log in to <strong>Kerio</strong> MailServer. If the password is stored in the SHA format, disableall methods but LOGIN and PLAIN.Operational system Authentication againstActive DirectoryUser mailboxesare stored locallyand passwordsare secured byDES encryptionUser mailboxesare stored locallyand passwordsare secured bySHA encryptionMS WindowsNTLMCRAM-MD5LOGINLOGINDIGEST-MD5PLAINPLAINLOGINPLAINLINUXLOGINCRAM-MD5LOGINPLAINDIGEST-MD5PLAINLOGINPLAINMac OS XLOGINCRAM-MD5LOGINPLAINDIGEST-MD5PLAINLOGINPLAINTable 15.3Authentication methodsFurther recommendations:• If a client authentication method fails, it is recommended to disable it in <strong>Kerio</strong> MailServer(uncheck it in the Enabled authentication methods list).• For all authentication methods, it is recommended to enable SSL login to the mail clients.Check Allow NTLM authentication for users with Kerberos authentication to allow users fromActive Directory to authenticate when attempting to log in to <strong>Kerio</strong> MailServer. In order for theNTLM authentication to be functional, both the computer as well as the user account have tobe parts of the domain used for authentication. The NTLM (SPA) authentication must be alsoenabled in users’ mail clients.To see what is necessary to be set in <strong>Kerio</strong> MailServer to make NTLM authentication worksmoothly, refer to chapter 25.In the Account lockout section the following parameters can be defined (see figure 15.19):Enable account lockoutWhen this option is selected, user accounts will be locked based on the following rules.These settings protect the user accounts from being misused.161