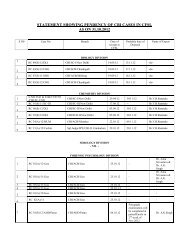
- Page 1 and 2:
Page 1 of 1
- Page 3 and 4:
Chapter 42 Drafting of Communicatio
- Page 5 and 6:
other Central Acts. A growing need
- Page 7 and 8:
y the Ministry of Home Affairs. Sub
- Page 9 and 10:
1.14 Directorate of ProsecutionThe
- Page 11 and 12:
absconders and fugitives as well as
- Page 13 and 14:
direct recruitment unless the Emplo
- Page 15 and 16:
2.3.10 An employee appointed on dep
- Page 17 and 18:
2.3.13 Premature Reversion of Deput
- Page 19 and 20:
2.6 Casual Appointments 4[4]2.6.1 C
- Page 21 and 22:
Employment Exchange. They should no
- Page 23 and 24:
2.7.3 Authority Competent to make C
- Page 25 and 26:
3.4 Supply of Blank Identity CardsB
- Page 27 and 28:
3.12 Destruction of Identity CardsA
- Page 29 and 30:
Tour)TOTAL 1 year &14weeks1 year &
- Page 31 and 32:
(i)To acquaint the recruits with th
- Page 33 and 34:
Officers by the JD(Admn.) and of th
- Page 35 and 36:
5. SERVICE RECORDS5.1 Service book
- Page 37 and 38:
(vii)Professional and technical qua
- Page 39 and 40:
his signature there in token of the
- Page 41 and 42:
6. CONFIRMATION6.1 As per the prese
- Page 43 and 44:
7. SENIORITY7.1 Fixation of Seniori
- Page 45 and 46:
ecruits or promotees, as the case m
- Page 47 and 48:
deployment in the latter office, wo
- Page 49 and 50:
8. ANNUAL CONFIDENTIAL REPORTS8.1 T
- Page 51 and 52:
non-initiation certificate in this
- Page 53 and 54:
should be rewarded by excessively f
- Page 55 and 56:
In the circumstances, where on cons
- Page 57 and 58:
9. PROMOTION9.1 The regular promoti
- Page 59 and 60:
seniority) is dispensed with and th
- Page 61 and 62:
9.9.2 In cases where the reasons ad
- Page 63 and 64:
10. FIXATION OF PAY10.1 Various pro
- Page 65 and 66:
10.4.2 Thus on comparing the positi
- Page 67 and 68:
(b) In the above case, if he opts t
- Page 69 and 70:
(ii)In the case where pay scales ar
- Page 71 and 72:
deputation/foreign service, even if
- Page 73 and 74:
selection, he/she is required to re
- Page 75 and 76:
13. LEAVE13.1 Provisions relating t
- Page 77 and 78:
certificate of fitness in accordanc
- Page 79 and 80:
(v)E.L. can be availed upto:(a) 180
- Page 81 and 82:
13.4 Commuted Leave(i) Commuted lea
- Page 83 and 84:
(iv)LND should not be granted as le
- Page 85 and 86:
(h)No Leave salary is admissible fo
- Page 87 and 88:
to leave salary during half pay lea
- Page 89 and 90:
sporting events subject to the over
- Page 91 and 92:
13.16 Encashment of Half Pay Leave:
- Page 93 and 94:
Request for leave will be considere
- Page 95 and 96:
(ii)(iii)(iv)(v)(vi)(vii)(viii)The
- Page 97 and 98:
accordance with the provisions of R
- Page 99 and 100:
Government servant who opts to reti
- Page 101 and 102:
ten years. It is calculated at the
- Page 103 and 104:
15.15.2 No gratuity shall be paid u
- Page 105 and 106:
three months pay or Rs.8000/- which
- Page 107 and 108:
dies before the date of retirement
- Page 109 and 110:
date of retirement in which case au
- Page 111 and 112:
16. DECENTRALIZATION OF ACCOUNTS16.
- Page 113 and 114:
PAO/CBI after checking of bills, in
- Page 115 and 116:
(c) re-appropriation of funds excee
- Page 117 and 118:
17.4.2 Motor vehicles owned by the
- Page 119 and 120:
18.4.3 A monthly expenditure statem
- Page 121 and 122:
19. ALLOWANCES AND REWARDS/HONORARI
- Page 123 and 124:
qualifying limits of the city/urban
- Page 125 and 126:
including civilian employees paid o
- Page 127 and 128:
(i)(ii)(iii)the normal one hour of
- Page 129 and 130:
promotion/reversion or revision of
- Page 131 and 132:
The Toll tax charged at any station
- Page 133 and 134:
ut the daily allowance drawn for th
- Page 135 and 136:
duty/leave/suspension depending on
- Page 137 and 138:
19.16 Railway WarrantsRailway Warra
- Page 139 and 140:
Officer should be kept in the servi
- Page 141 and 142:
can be sanctioned by Addl.Director,
- Page 143 and 144:
20. ADVANCES20.1 Advances are provi
- Page 145 and 146:
(flood/drought/cyclone) and granted
- Page 147 and 148:
An advance not exceeding the travel
- Page 149 and 150:
When an advance is granted to an em
- Page 151 and 152:
2001-02 13 9.5 7.02002-03 12.5 9.0
- Page 153 and 154:
h) Advance can be granted only if t
- Page 155 and 156:
e) The advance can also be given on
- Page 157 and 158:
) Constructing a new house on a plo
- Page 159 and 160:
5 For constructionThe advance shoul
- Page 161 and 162:
ii)iii)iv)The second charge can be
- Page 163 and 164:
(iii)City Compensatory Allowance(iv
- Page 165 and 166:
(iii)Cycle Advance(iv)Motor Cycle A
- Page 167 and 168:
22. CONTINGENCIES22.1 Contingencies
- Page 169 and 170:
nomination that the nomination will
- Page 171 and 172:
advance and the total consolidated
- Page 173 and 174:
(viii)Pass Books are to be issued t
- Page 175 and 176:
24.3 The balance for March every ye
- Page 177 and 178:
drought etc. and his financial posi
- Page 179 and 180:
advance should be adjusted within s
- Page 181 and 182:
now eligible to retain the governme
- Page 183 and 184:
26. DEPARTMENTAL CANTEEN26.1 Meetin
- Page 185 and 186: Register/Sanitary Diary. A suggesti
- Page 187 and 188: 27. MEDICAL FACILITES TO THE CENTRA
- Page 189 and 190: 4. Cantonment hospitals in cantonme
- Page 191 and 192: and their family members residing i
- Page 193 and 194: ii) X-Ray, Laboratory and other dia
- Page 195 and 196: office concerned will correspond wi
- Page 197 and 198: Group ofEmployeesSubscription per m
- Page 199 and 200: (b)(c)(d)if there is no valid nomin
- Page 201 and 202: ) While selecting the site, it shou
- Page 203 and 204: safaiwala, cleaning work can be got
- Page 205 and 206: contract awarded to another firm of
- Page 207 and 208: vi)Responsibility and accountabilit
- Page 209 and 210: (x)(xi)(xii)(xiii)(xiv)(xv)(xvi)Whe
- Page 211 and 212: i) Verification shall always be mad
- Page 213 and 214: 31. FURNITURE31.1 The furniture wil
- Page 215 and 216: Sl.NomenclatureScaleNo.1 Officer’
- Page 217 and 218: i) For rooms having area upto 30 sq
- Page 219 and 220: charges are to be deposited by the
- Page 221 and 222: 33.6 Officers of the rank of Joint
- Page 223 and 224: All 4-wheelers should be got servic
- Page 225 and 226: 33.19 All requisitions for the vehi
- Page 227 and 228: 34.5 No dues certificate from Libra
- Page 229 and 230: 35. SECURITY PLAN35.1 In view of th
- Page 231 and 232: inner entry point. Similarly, all v
- Page 233 and 234: 35.6.3 The local fire service can b
- Page 235: 35.7.3 Transit of documents and des
- Page 239 and 240: 35.9.9 The attack or crisis control
- Page 241 and 242: 35.10.10 Blood groups of all the st
- Page 243 and 244: 36.7 'Central receipt and issue sec
- Page 245 and 246: 36.31 'Note' means the remarks reco
- Page 247 and 248: 37. MACHINERY OF GOVERNMENT37.1 The
- Page 249 and 250: consists of assistants and clerks s
- Page 251 and 252: CR No..............................
- Page 253 and 254: 39. RECEIPT-SUBMISSION AND DIARISAT
- Page 255 and 256: (ii)The Section Officer/OS/Head Cle
- Page 257 and 258: (xiv)put up the case to the appropr
- Page 259 and 260: notes.If he agrees to the line of a
- Page 261 and 262: 40.11 Oral discussions(i)All points
- Page 263 and 264: ing to the notice of the branch off
- Page 265 and 266: one FRs, they should be flagged sep
- Page 267 and 268: 41. FORMS AND PROCEDURE OFCOMMUNICA
- Page 269 and 270: (x) Endorsement :This form is used
- Page 271 and 272: (i) the originating Ministry should
- Page 273 and 274: should ordinarily be preceded by in
- Page 275 and 276: eplies have not been received, may
- Page 277 and 278: (vi)All drafts put up on a file sho
- Page 279 and 280: 43. ISSUE OF DRAFTS43.1 Marking of
- Page 281 and 282: (iii)At the end of the day, the cle
- Page 283 and 284: (iv)Separate the communications to
- Page 285 and 286: maintenance of service postage stam
- Page 287 and 288:
(iii)The Branch officer in charge o
- Page 289 and 290:
44. FILING SYSTEM44.1 Filing system
- Page 291 and 292:
(d)the factors to be taken into con
- Page 293 and 294:
(ii) Movement of files received fro
- Page 295 and 296:
(e) arrange the index slips in two
- Page 297 and 298:
(d) in respect of records connected
- Page 299 and 300:
(a) complete columns 4 & 5 of the f
- Page 301 and 302:
eview in the preceding year togethe
- Page 303 and 304:
46. SECURITY OF OFFICIAL INFORMATIO
- Page 305 and 306:
47. CHECKS ON DELAYS47.1 Weekly arr
- Page 307 and 308:
(a) scrutinise the case sheets and
- Page 309 and 310:
(b) prepare the consolidated statem
- Page 311 and 312:
47.9 Responsibility of expeditious
- Page 313 and 314:
(iv) A register of Identification C
- Page 315 and 316:
Pension Payment order (PPO) was not
- Page 317 and 318:
49. INSPECTIONS49.1 Meaning & Purpo
- Page 319 and 320:
49.7.1 Attendance Register - Whethe
- Page 321 and 322:
(b) items pending for actual payee
- Page 323 and 324:
49.10.6 Diaries and Progress Report
- Page 325 and 326:
xv)xvi)xvii)xviii)xix)xx)xxi)xxii)x
- Page 327 and 328:
(xiii) Stock Registers :a) Consumab
- Page 329 and 330:
(a) he has passed the Matriculation
- Page 331 and 332:
APPENDIX-IPOSTS SANCTIONED IN CBI A
- Page 333 and 334:
DPA Gr.B 1 Rs.6500-200-10500/-DPA G
- Page 335 and 336:
x. To liaise with all officers/Sect
- Page 337 and 338:
iii. Supervision, caretaking etc.,
- Page 339 and 340:
APPENDIX-IIIRECRUITMENT RULES1. Int
- Page 341 and 342:
(ix) Fifty percent posts of ASIs ar
- Page 343 and 344:
appointmentCentral Government Offic
- Page 345 and 346:
APPENDIX-IVAPPOINTMENT THROUGH STAF
- Page 347 and 348:
APPENDIX-VTHE DELHI SPECIAL POLICE
- Page 349 and 350:
shall be deemed to have been suspen
- Page 351 and 352:
7. DISCIPLINARY AUTHORITIES:(1) The
- Page 353 and 354:
(9) The Disciplinary Authority shal
- Page 355 and 356:
11. SPECIAL PROCEDURE IN CERTAIN CA
- Page 357 and 358:
without holding an inquiry at all a
- Page 359 and 360:
the appellant relies; shall not con
- Page 361 and 362:
PROVIDED THAT-(i) the appellate aut
- Page 363 and 364:
PART-VI- MISCELLANEOUS27. THE CENTR
- Page 365 and 366:
SCHEDULEDescriptionof rank orpost1A
- Page 367 and 368:
SCHEDULEDescription ofpost1Part-I -
- Page 369 and 370:
SCHEDULEPart-III- General Central S
- Page 371 and 372:
It will aid the recruitment/promoti
- Page 373 and 374:
Annexure - INo.4/31/61-TGOVERNMENT
- Page 375 and 376:
Encl. To Annexure-IIINVESTIGATION A
- Page 377 and 378:
IV.RESEARCH DIVISION.(1) Analysis a
- Page 379 and 380:
Annexure - IIINo.21/43/2002-PD-0130
- Page 381 and 382:
WEST ZONE10 Anti-CorruptionRegion-I
- Page 383 and 384:
SP/ACB/Guwahati27 Anti-Corruption B
- Page 385 and 386:
Union Territoriesof Pondicherry and
- Page 387 and 388:
SP EOU-II, EO-I(Existing SP-II/SIG/
- Page 389 and 390:
77 Special Unit KolkataSP SU Kolkat
- Page 391 and 392:
(b) Horizontal Reservation :(i) Whe
- Page 393 and 394:
(f) (i) The post for which this req
- Page 395 and 396:
Investigation includingappreciation
- Page 397 and 398:
Annexure - VICHECKLIST OF POINTS FO
- Page 399 and 400:
Annexure - VIIMOST IMMEDIATENo.DP A
- Page 401 and 402:
STATEMENT SHOWING THE FINANCIAL AND
- Page 403 and 404:
the Central Civil Services(Pension)
- Page 405 and 406:
MODEL CALCULATION - 2PENSION, COMMU
- Page 407 and 408:
Annexure - X(A)No.240/1/96-AVD.IIGO
- Page 409 and 410:
4 Electric Gas and WaterCharges.5 F
- Page 411 and 412:
9 Engagement of Spl.Counsel on beha
- Page 413 and 414:
(ii) For residential andother purpo
- Page 415 and 416:
28 CONTINGENTEXPENDITURE (Table inS
- Page 417 and 418:
ToThe Director,Central Bureau of in
- Page 419 and 420:
Annexure - XI(A)No. 29/1/96-AD.IIIC
- Page 421 and 422:
The delegation of financial powers
- Page 423 and 424:
(b)i) APP, Gr-B (Non-Gazetted) Rs.
- Page 425 and 426:
Other Govt. Servants - As considere
- Page 427 and 428:
To,1. PS to Director, CBI.2. Ps to
- Page 429 and 430:
7Legal Charges/ otherlegal charges(
- Page 431 and 432:
paymentof localand trunkcalls andre
- Page 433 and 434:
24 Incurring of--- RecurringMiscell
- Page 435 and 436:
irthvest only with-Director /CBIbei
- Page 437 and 438:
pay and allowancestherefore(Ministr
- Page 439 and 440:
than those mentionedin SRs. 130 and
- Page 441 and 442:
RPS dated 30.11.5671 Appointment of
- Page 443 and 444:
to which Govt. is a-party ( Rule 25
- Page 445 and 446:
joining time inrelaxation of provis
- Page 447 and 448:
115 House buildingadvance to office
- Page 449 and 450:
Authorised MedicalAttendant would n
- Page 451 and 452:
Annexure - XIVG.I, Dte. of Estates
- Page 453 and 454:
(II)NON-CONVENTIONAL SPACESl. No. P
- Page 455 and 456:
(M.K. Nair)Deputy Financial Adviser
- Page 457 and 458:
(ii)(iii)(iv)The officer using the
- Page 459 and 460:
to the wall or partition. The top o
- Page 461 and 462:
(c) All occupants of the building s
- Page 463 and 464:
Annexure - XIXASSISTANT’S DIARYSl
- Page 465 and 466:
4. The correctness of the entries o
- Page 467 and 468:
Annexure - XXIIPRECEDENT BOOKHeadin
- Page 469 and 470:
Annexure - XXIII(B)No.84/5/62-Estt.
- Page 471 and 472:
SPECIAL POLICE ESTABLISHMENTSTATEME
- Page 473 and 474:
36 Property returns andcorresponden
- Page 475 and 476:
88 TA Bill Register. 10 years.89 Ma
- Page 477 and 478:
21 Supply of stationery and forms 3
- Page 479 and 480:
STATEMENT SHOWING THE PERIODS FOR W
- Page 481 and 482:
Annexure - XXIII(E)No.40/86/69-AD.I
- Page 483 and 484:
17 Correspondence regarding HouseBu
- Page 485 and 486:
Annexure - XXIVREGISTER FOR WATCHIN
- Page 487 and 488:
Annexure - XXVILIST OF FILES DUE FO
- Page 489 and 490:
5. 4. The same form will be used to
- Page 491 and 492:
Annexure - XXIXCASE SHEETFile/Diary
- Page 493 and 494:
Annexure - XXXINUMERICAL ABSTRACT O
- Page 495 and 496:
Annexure - XXXIIMONTHLY PROGRESS RE
- Page 497 and 498:
Annexure - XXXIVCHECK LIST FOR WATC