Secure Grid Computing - GridSec Project - University of Southern ...
Secure Grid Computing - GridSec Project - University of Southern ...
Secure Grid Computing - GridSec Project - University of Southern ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
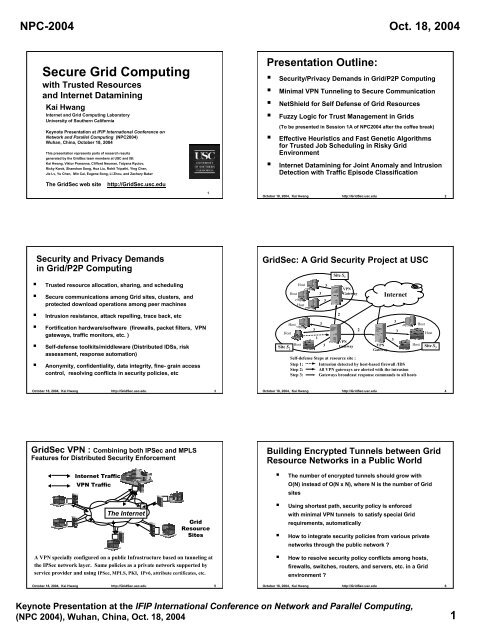
NPC-2004 Oct. 18, 2004<br />
<strong>Secure</strong> <strong>Grid</strong> <strong>Computing</strong><br />
with Trusted Resources<br />
and Internet Datamining<br />
Kai Hwang<br />
Internet and <strong>Grid</strong> <strong>Computing</strong> Laboratory<br />
<strong>University</strong> <strong>of</strong> <strong>Southern</strong> California<br />
Keynote Presentation at IFIP International Conference on<br />
Network and Parallel <strong>Computing</strong> (NPC2004)<br />
Wuhan, China, October 18, 2004<br />
This presentation represents parts <strong>of</strong> research results<br />
generated by the <strong>Grid</strong>Sec team members at USC and ISI:<br />
Kai Hwang, Viktor Prasanna, Clifford Neuman, Tatyana Ryutov,<br />
Ricky Kwok, Shanshan Song, Hua Liu, Rohit Tripathi, Ying Chen,<br />
Jie Lv, Yu Chen, Min Cai, Eugene Song, Li Zhou, and Zachary Baker<br />
The <strong>Grid</strong>Sec web site<br />
http://<strong>Grid</strong>Sec.usc.edu<br />
Presentation Outline:<br />
• Security/Privacy Demands in <strong>Grid</strong>/P2P <strong>Computing</strong><br />
• Minimal VPN Tunneling to <strong>Secure</strong> Communication<br />
• NetShield for Self Defense <strong>of</strong> <strong>Grid</strong> Resources<br />
• Fuzzy Logic for Trust Management in <strong>Grid</strong>s<br />
(To be presented in Session 1A <strong>of</strong> NPC2004 after the c<strong>of</strong>fee break)<br />
• Effective Heuristics and Fast Genetic Algorithms<br />
for Trusted Job Scheduling in Risky <strong>Grid</strong><br />
Environment<br />
• Internet Datamining for Joint Anomaly and Intrusion<br />
Detection with Traffic Episode Classification<br />
1<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
2<br />
Security and Privacy Demands<br />
in <strong>Grid</strong>/P2P <strong>Computing</strong><br />
<strong>Grid</strong>Sec: A <strong>Grid</strong> Security <strong>Project</strong> at USC<br />
• Trusted resource allocation, sharing, and scheduling<br />
• <strong>Secure</strong> communications among <strong>Grid</strong> sites, clusters, and<br />
protected download operations among peer machines<br />
Host<br />
Host<br />
Host<br />
3<br />
3<br />
3<br />
VPN<br />
Gateway<br />
Site S 1<br />
3<br />
Internet<br />
• Intrusion resistance, attack repelling, trace back, etc<br />
• Fortification hardware/s<strong>of</strong>tware (firewalls, packet filters, VPN<br />
gateways, traffic monitors, etc. )<br />
• Self-defense toolkits/middleware (Distributed IDSs, risk<br />
assessment, response automation)<br />
• Anonymity, confidentiality, data integrity, fine- grain access<br />
control, resolving conflicts in security policies, etc<br />
2<br />
Host<br />
3<br />
3<br />
Host<br />
Host<br />
3<br />
2<br />
3<br />
Host<br />
1<br />
3<br />
VPN<br />
Host<br />
3<br />
Site S 2<br />
Gateway<br />
VPN<br />
Gateway<br />
Host Site S 3<br />
Self-defense Steps at resource site :<br />
Step 1: Intrusion detected by host-based firewall /IDS<br />
Step 2: All VPN gateways are alerted with the intrusion<br />
Step 3: Gateways broadcast response commands to all hosts<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
3<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
4<br />
<strong>Grid</strong>Sec VPN : Combining both IPSec and MPLS<br />
Features for Distributed Security Enforcement<br />
Internet Traffic<br />
VPN Traffic<br />
Building Encrypted Tunnels between <strong>Grid</strong><br />
Resource Networks in a Public World<br />
• The number <strong>of</strong> encrypted tunnels should grow with<br />
O(N) instead <strong>of</strong> O(N x N), where N is the number <strong>of</strong> <strong>Grid</strong><br />
sites<br />
The Internet<br />
<strong>Grid</strong><br />
Resource<br />
Sites<br />
• Using shortest path, security policy is enforced<br />
with minimal VPN tunnels to satisfy special <strong>Grid</strong><br />
requirements, automatically<br />
• How to integrate security policies from various private<br />
networks through the public network <br />
A VPN specially configured on a public Infrastructure based on tunneling at<br />
the IPSec network layer. Same policies as a private network supported by<br />
service provider and using IPSec, MPLS, PKI, IPv6, attribute certificates, etc.<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
5<br />
• How to resolve security policy conflicts among hosts,<br />
firewalls, switches, routers, and servers, etc. in a <strong>Grid</strong><br />
environment <br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
6<br />
Keynote Presentation at the IFIP International Conference on Network and Parallel <strong>Computing</strong>,<br />
(NPC 2004), Wuhan, China, Oct. 18, 2004 1
NPC-2004 Oct. 18, 2004<br />
Trust Integration over a VPN Ring<br />
Aggregate costs in Single Sign-on<br />
operation over VPN vs. PKI Services<br />
V<br />
V<br />
Site S 2<br />
Site S 1<br />
Site S 4<br />
V<br />
SeGO<br />
Server<br />
VPN<br />
Gateway<br />
Hosts<br />
Site S 3<br />
Physical backbone<br />
VPN tunnel ring<br />
V Trust Vector<br />
Trust vector<br />
propagation<br />
User application<br />
and SeGO server<br />
negotiation<br />
Cooperating gateways working together<br />
to establish VPN tunnels for trust integration<br />
V<br />
Aggregate Service Cost<br />
10<br />
8<br />
6<br />
4<br />
GSI based<br />
VPN based<br />
2<br />
0<br />
10 20 30 40 50 60 70 80 90 100<br />
<strong>Grid</strong> Size<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
7<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
8<br />
Global <strong>Grid</strong>Sec Testing Environment<br />
International Collaborators in USA,<br />
France, China, and Australia<br />
USC NetShield Intrusion Defense System<br />
for Protecting Local Network<br />
<strong>of</strong> <strong>Grid</strong> <strong>Computing</strong> Resources<br />
INRIA,<br />
Sophia<br />
Antipolis,<br />
France<br />
ICT <strong>of</strong> CAS<br />
Beijing,<br />
China<br />
Melbourne<br />
<strong>University</strong>,<br />
Australia<br />
The <strong>Grid</strong>Sec<br />
over Internet<br />
USC Gateway,<br />
Los Angeles<br />
Trojan<br />
Cluster in<br />
IGC Lab.<br />
USC/ISD<br />
Supercluster<br />
USC NetShield Defense<br />
System and Testing<br />
Facilities<br />
Security<br />
Policy<br />
Manager<br />
Security<br />
Database<br />
ISP<br />
The<br />
Internet<br />
Network<br />
Router<br />
The<br />
NetShield<br />
System<br />
Firewall<br />
Datamining for Anomaly<br />
Intrusion Detection (IDS)<br />
Risk<br />
Assessment<br />
System (RAS)<br />
Intrusion<br />
Response<br />
System (IRS)<br />
Victim’s<br />
Internal<br />
Network<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
9<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
10<br />
Security-Driven Heuristics for Trusted Job<br />
Scheduling on Risky <strong>Grid</strong>s<br />
• Min-min heuristics:<br />
‣ For each job, the resource site that gives the earliest completion time is<br />
selected first. The job that has the minimum earliest completion time is<br />
assigned to the selected resource site.<br />
• Sufferage heuristics:<br />
‣ The Sufferage heuristic is based on the idea that better mappings are<br />
generated by assigning a site to a job that would “suffer” most in terms <strong>of</strong><br />
expected completion time<br />
• Three secure and risky scheduling modes:<br />
‣ <strong>Secure</strong> mode – Allocate jobs only to those <strong>Grid</strong> sites with security level<br />
exceeding the job requirement (SD < SL)<br />
‣ Risky mode – Allocate jobs to any available <strong>Grid</strong> sites without checking<br />
the risk level or the job demand<br />
‣ f-risky mode – Allocate jobs to those <strong>Grid</strong> sites taking at most f % risk<br />
Risk scale:<br />
0 f 100%<br />
( ) 0 P fail = P( fail)<br />
f<br />
P( fail )
NPC-2004 Oct. 18, 2004<br />
The bad things always happen --- Murphy’s Law<br />
Historical<br />
database<br />
We are scared.<br />
Let us just wait<br />
…<br />
☺☺<br />
☺<br />
☺ ☺<br />
☺<br />
☺<br />
☺ ☺ ☺<br />
☺☺<br />
☺☺☺☺☺☺☺<br />
We don’t care, just do<br />
it. I am courageous, not<br />
a kid anymore,….<br />
☺<br />
☺<br />
☺ ☺ ☺<br />
☺<br />
☺<br />
☺ ☺ ☺<br />
Decreasing security demands<br />
(SD) from user jobs<br />
Decreasing security level (SL), assured<br />
by <strong>Grid</strong> sits or increasing risk levels<br />
I will run a calculated<br />
risk, but wait a while …<br />
☺<br />
☺ ☺ ☺<br />
☺<br />
☺<br />
☺ ☺ ☺<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
13<br />
☺<br />
I calculate<br />
too, maybe I<br />
am lucky …<br />
(a) <strong>Secure</strong> Mode (b) Risky mode (c) f-risky mode<br />
NAS and PSA Workloads :<br />
• Parameters in Two Real Workloads:<br />
‣ NAS (Numerical Aerodynamic Simulation)<br />
Workload:<br />
• Resource sites: 12 sites (8: 8 nodes/site,<br />
4: 16 nodes/site)<br />
• Jobs: arrival time and workload from the trace file<br />
• N = 16,000 jobs running on M = 12 <strong>Grid</strong> sites<br />
‣ Parameter Sweep Application (PSA) Workload:<br />
• Site processing speed:10 levels, M = 20 sites<br />
• Job workload: 20 levels, N = 5,000 jobs<br />
• Job arrival: Poisson distribution 0.008 jobs/sec<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
14<br />
Difference between Traditional GA and<br />
Space-Time Genetic Algorithms (STGA)<br />
in Term <strong>of</strong> Solution Quality<br />
--- Fast scheduling and easy to implement<br />
Solution<br />
Quality<br />
Generate random<br />
initial population<br />
STGA<br />
starting point<br />
GA<br />
STGA<br />
Good<br />
solution<br />
is found<br />
Evolution<br />
Iterations<br />
The starting point is based on prior solution database.<br />
Genetic Algorithms (GA)<br />
• Genetic Algorithms (GAs) are a popular technique used in<br />
search <strong>of</strong> large solution spaces.<br />
• GA is studied for job scheduling in heterogeneous<br />
computing and <strong>Grid</strong> environments.<br />
‣ It is powerful for generating some good solutions.<br />
‣ It is not widely used for its long computational time<br />
(overhead)<br />
How GA works<br />
0<br />
1<br />
0<br />
1<br />
0<br />
1<br />
1<br />
0<br />
0<br />
1<br />
0<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
0.3 0.6 0.9 0.6<br />
Initial Population<br />
0<br />
0<br />
0<br />
1<br />
0<br />
1<br />
1<br />
0<br />
0<br />
1<br />
0<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
0.9 0.6 0.9 0.6<br />
After selection<br />
0<br />
0<br />
0<br />
0<br />
1<br />
1<br />
1<br />
0<br />
1<br />
0<br />
0<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
1.0 0.4 0.9 0.6<br />
After crossover<br />
0<br />
0<br />
0<br />
0<br />
1<br />
1<br />
1<br />
0<br />
1<br />
0<br />
1<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
0<br />
0<br />
1<br />
1.0 0.4 0.8 0.6<br />
After mutation<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
15<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
16<br />
Simulation <strong>of</strong> The Space-Time<br />
Genetic Algorithm (STGA)<br />
• STGA parameters:<br />
‣ Training data: 500 jobs<br />
‣ Look table size = 150<br />
‣ Initial population size = 200<br />
‣ Evolution times = 100 iterations<br />
• Compared with 1000 used in traditional GA<br />
‣ Crossover probability = 0.8<br />
‣ Mutation probability = 0.01<br />
The Total Execution Time <strong>of</strong> 16,000 jobs<br />
on 12 <strong>Grid</strong> sites with 8 or 16 nodes per site<br />
--- Makespan in seconds under the NAS Workload with<br />
uniform distributions on site security level (0.4 – 1.0)<br />
and on job security demand (0.6 – 0.9)<br />
Makespan (seconds)<br />
7x10 6<br />
6x10 6<br />
5x10 6<br />
4x10 6<br />
3x10 6<br />
2x10 6<br />
1x10 6<br />
0<br />
1 2 3 4 5 6 7<br />
Min-min<br />
<strong>Secure</strong><br />
Min-Min<br />
f-Risky<br />
Min-min<br />
Risky<br />
Sufferage<br />
<strong>Secure</strong><br />
Sufferage<br />
f-Risky<br />
Sufferage<br />
Risky<br />
STGA<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
17<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
18<br />
Keynote Presentation at the IFIP International Conference on Network and Parallel <strong>Computing</strong>,<br />
(NPC 2004), Wuhan, China, Oct. 18, 2004 3
NPC-2004 Oct. 18, 2004<br />
Relative Performance <strong>of</strong> Three Scheduling<br />
Algorithms on the NAS Workload under<br />
Three Different Risky Conditions<br />
Scheduling Algorithms Makespan (sec) Ave. Rsp. Time (sec) Ranking<br />
The Total Execution Time <strong>of</strong> 5,000 jobs<br />
on 20 <strong>Grid</strong> sites with10 levels <strong>of</strong> site speed<br />
--- Makespan in second under the PSA workload with uniform<br />
distributions on the site security level (0.4 – 1.0) and on the job<br />
security demand (0.6-0.9)<br />
Min-Min <strong>Secure</strong> 6491186 131% 1308360 203% ≈ 4 th<br />
0.5-Risky 5714605 115 % 926952 144 % ≈ 3 rd<br />
Risky 5402546 109 % 811873 126 % ≈ 2 nd<br />
Sufferage <strong>Secure</strong> 6454823 130 % 1292948 201 % ≈ 4 th<br />
0.5-Risky 5834757 118 % 999765 155 % ≈ 3 rd<br />
Risky 5441722 110 % 819667 127 % ≈ 2 nd<br />
STGA 4939777 100 % 643076 100 % 1 st<br />
Makespan(seconds)<br />
2.0x10 6<br />
1.5x10 6<br />
1.0x10 6<br />
5.0x10 5<br />
0.0<br />
Min-min<br />
1 2 3 4 5 6 7<br />
<strong>Secure</strong><br />
Min-min<br />
f-Risky<br />
Min-min<br />
Risky<br />
Sufferage<br />
<strong>Secure</strong><br />
Sufferage<br />
f-<strong>Secure</strong><br />
Sufferage<br />
Risky<br />
STGA<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
19<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
20<br />
Total <strong>Grid</strong> Site Resource Utilization (%)<br />
Basic Concept <strong>of</strong> Internet Episodes<br />
--- Plotted for a partially risky situation with f = 0.5<br />
under the PSA workload distributed to 20 <strong>Grid</strong> sites<br />
100<br />
• Event Type: A, B, C, D, E, F, etc.<br />
Site Utilization (%)<br />
80<br />
60<br />
40<br />
20<br />
0<br />
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20<br />
<strong>Grid</strong> Resource Site<br />
Min-Min f-risky<br />
Sufferage f-risky<br />
STGA<br />
• Event Sequence: e.g., <br />
• Window: Event sequence with a particular width<br />
• Episode: partially ordered set <strong>of</strong> events, e.g. whenever A occurs, B<br />
will occur soon<br />
• Frequency <strong>of</strong> episode: fraction <strong>of</strong> windows in which episode occurs<br />
• Frequent episode: set <strong>of</strong> episodes having a frequency over a<br />
particular frequency threshold<br />
• Frequent episode rules are generated to describe the<br />
connection events<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
21<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
22<br />
Frequent Episode Rules (FER)<br />
for Characterizing Network Traffic Connections<br />
E → D, F ( c, s )<br />
The episode <strong>of</strong> 3 connection events (E, D, F) = (http, smpt, telent).<br />
On the LHS , we have the event E (http). On the RHS, we have two<br />
consequence events D (smpt) and F(telnet); where s is the<br />
support probablity and c is the confidence level specified below:<br />
(service = http, flag = SF) →<br />
(service = smpt, srcbyte = 5000),<br />
(service = telnet, flag = SF) (0.8, 0.9)<br />
Support probability s = 0.9 and Confidence level c = 0.8 that the<br />
episode will take place in a typical traffic stream<br />
The JAIDS Architecture<br />
Audit records<br />
from traffic data<br />
Known<br />
attack<br />
signatures<br />
from ISD<br />
provider<br />
Single-connection attacks<br />
detected at packet level<br />
IDS<br />
Signature<br />
Matching<br />
Engine<br />
Attack<br />
Signature<br />
Database<br />
Unknown<br />
or burst<br />
attacks<br />
New<br />
signatures<br />
from<br />
anomalies<br />
detected<br />
Episode Rule<br />
Database<br />
ADS<br />
Training data from<br />
audit normal traffic<br />
records<br />
Episode<br />
Mining<br />
Engine<br />
ADS<br />
Signature<br />
Generator<br />
Anomalies detected<br />
over multiple<br />
connections<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
23<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
24<br />
Keynote Presentation at the IFIP International Conference on Network and Parallel <strong>Computing</strong>,<br />
(NPC 2004), Wuhan, China, Oct. 18, 2004 4
NPC-2004 Oct. 18, 2004<br />
Internet Datamining<br />
for Episode Rule Generation<br />
Attack Spectrum<br />
in 10 Days <strong>of</strong> Experimentation<br />
Audit data<br />
Feature<br />
extraction<br />
Connection<br />
Records<br />
Episode rule<br />
mining Engine<br />
Training<br />
phase<br />
Detection<br />
phase<br />
Attack-free<br />
episode rules<br />
Rules from<br />
real-time<br />
traffic<br />
Normal<br />
pr<strong>of</strong>ile<br />
database<br />
Anomaly<br />
Detection<br />
Engine<br />
Alarm<br />
Generation<br />
Attack numbers<br />
20<br />
15<br />
10<br />
5<br />
0<br />
Day1 Day2 Day3 Day4 Day5 Day6 Day7 Day8 Day9 Day10<br />
Days<br />
DoS<br />
U2R<br />
R2L<br />
Probe<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
25<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
26<br />
Automated Signature Generation<br />
1. Label relevant connections to<br />
associate with an FER.<br />
Online traffic episode rules<br />
from the datamining engine<br />
Success Rates <strong>of</strong> Snort (a Network IDS), a<br />
Pure Anomaly Detection System (ADS), and the<br />
Joint Anomaly and Intrusion Detection System (JAIDS)<br />
Yes<br />
Episode Frequency<br />
exceeding the rule<br />
threshold <br />
No<br />
Yes (Massive attacks)<br />
2 Calculate additional information such<br />
as connection count, average and<br />
percentage <strong>of</strong> connections, etc.<br />
3 Select one <strong>of</strong> the predefined classifiers<br />
4 Use the selected classifier to classify the attack<br />
class and find the relevant connections<br />
5 Extract common features in all identified<br />
connections, such as the IP addresses, protocol,<br />
etc. to form the signature<br />
Episode rules<br />
matching the normal<br />
FER database <br />
No (Stealthy attacks)<br />
2 Check error flags or other useful<br />
temporal statistics<br />
3 Extract common features such<br />
as IP addresses, protocol, etc.<br />
to form the signature<br />
Adding new<br />
signatures to the<br />
Snort database<br />
Ignore the normal episode rules from legitimate users (No anomaly detected)<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
27<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
28<br />
False Alarms out <strong>of</strong> 201 Attacks in JAIDS<br />
Triggered by Different Attack Types<br />
under Various Scanning Window Sizes<br />
Detection Rates <strong>of</strong> Snort (a Network IDS), a<br />
custom-designed Anomaly Detection System (ADS),<br />
Joint Anomaly/Intrusion Detection System (JAIDS)<br />
Number <strong>of</strong> False Alarms<br />
18<br />
16<br />
14<br />
12<br />
10<br />
8<br />
6<br />
4<br />
2<br />
0<br />
100 300 500 1000 7200<br />
Wi ndow Si ze (Second)<br />
R2L<br />
DoS<br />
Pr obe<br />
U2R<br />
Using larger windows result in more false alarms. Shorter windows in 300 sec<br />
or less are better in the sense that shorter episodes will be mined to produce<br />
shorter rules, leading to faster rule matching in the anomaly detection process<br />
Intrusion Detection<br />
Rate (%)<br />
70<br />
60<br />
50<br />
40<br />
30<br />
20<br />
10<br />
0<br />
DoS U2R R2L PROBE Tot a l<br />
At t a c k Type s<br />
SNORT<br />
ADS<br />
JAIDS<br />
On the average, the JAIDS (white bars) outperforms<br />
the Snort and ADS by 51% and 40%, respectively<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
29<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
30<br />
Keynote Presentation at the IFIP International Conference on Network and Parallel <strong>Computing</strong>,<br />
(NPC 2004), Wuhan, China, Oct. 18, 2004 5
NPC-2004 Oct. 18, 2004<br />
ROC Curves for 4 Attack Classes<br />
on The Simulated JAIDS<br />
ROC Performance <strong>of</strong> Three<br />
Intrusion Detection Systems<br />
Intrusion Detection Rate (%)<br />
80<br />
70<br />
60<br />
50<br />
40<br />
30<br />
20<br />
10<br />
0<br />
0 2 4 6 8 10 12<br />
False Alarm Rate (%)<br />
DoS<br />
Pr obe<br />
R2L<br />
U2R<br />
Intrusion Detection Rate<br />
(%)<br />
80<br />
70<br />
60<br />
50<br />
40<br />
30<br />
20<br />
10<br />
0<br />
0 2 4 6 8 10 12<br />
False Alarm Rate (%)<br />
JAIDS<br />
Snor t<br />
ADS<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
31<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
32<br />
Final Remarks:<br />
• The security-driven Min-Min and Sufferage heuristics and the<br />
new space-time genetic algorithm (STGA) are fast and easy to<br />
implement in a risky open <strong>Grid</strong> environment to yield<br />
satisfactory performance with low overhead.<br />
• The new Internet episode detection scheme (JAIDS) can cope<br />
with both known and unknown network attacks. This will<br />
secure many <strong>Grid</strong>/P2P operations in using common Internet<br />
services: telnet, http, ftp, smtp, Email, authentication, etc.<br />
• The NetShield self-defense IDS/IRD system is still under<br />
development at USC. For ultra security-sensitive <strong>Grid</strong> services,<br />
we recommend the use <strong>of</strong> dedicated VPN tunnels to secure <strong>Grid</strong><br />
communications and safeguard P2P download operations.<br />
Hot Research Thrust Areas:<br />
• Perfection <strong>of</strong> the trust models for protecting virtual<br />
organizations with scalable <strong>Grid</strong> applications without worry<br />
about infections or becoming victims by participating in<br />
collective operations – In particular, the fuzzy- and gametheoretical<br />
approaches are promising.<br />
• Large-scale benchmark experiments on open <strong>Grid</strong>s are<br />
desired to work out some semi-optimal solutions to real-life<br />
scientific and business <strong>Grid</strong> applications<br />
• Internet datamining for security control and for the guarantee<br />
<strong>of</strong> the Quality-<strong>of</strong>-Service in real-life <strong>Grid</strong> applications –<br />
Interoperability between wired and wireless <strong>Grid</strong>s is also a<br />
very hot issue.<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
33<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
34<br />
Recent Papers or Reports :<br />
1. K. Hwang, S. Song, and J. Lv, “ <strong>Grid</strong>Sec: <strong>Grid</strong> Security Enforcement with<br />
Trust Integration over Minimal VPN Tunnels”, USC Technical Report 2004 –13,<br />
IEEE Computer Magazine, submitted July 2004.<br />
2. S. Song, K. Hwang, and M. Macwan, “Fuzzy Trust Integration for Security<br />
Enforcement in <strong>Grid</strong> <strong>Computing</strong>”, Proc. <strong>of</strong> NPC 2004, Wuhan, China,<br />
October 18, 2004<br />
3. M. Qin and K. Hwang, “Frequent Episode Rules for Internet Traffic Analysis<br />
and Anomaly Detection”, IEEE Network <strong>Computing</strong> and Application Symp.<br />
(NCA-2004), Cambridge, MA. August 31, 2004<br />
4. K. Hwang, H. Liu, Y. Chen, and M.Qin,“ Protecting Network-Centric Systems<br />
with Joint Anomaly/Intrusion Detection over Internet Episodes”, USC<br />
Technical Report 2004 –17, submitted to IPDPS 2005, Oct.8, 2004<br />
Questions or Taking the C<strong>of</strong>fee Break <br />
5. S. Song, R. Kwok, and K. Hwang, “ Trusted Job Scheduling in Open<br />
Computational <strong>Grid</strong>s: Security-Driven Heuristics and A Fast Genetic<br />
Algorithm”, USC Technical Report 2004 –18, submitted to IPDPS 2005, Oct.8,<br />
2004<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
35<br />
October 18, 2004, Kai Hwang http://<strong>Grid</strong>Sec.usc.edu<br />
36<br />
Keynote Presentation at the IFIP International Conference on Network and Parallel <strong>Computing</strong>,<br />
(NPC 2004), Wuhan, China, Oct. 18, 2004 6