Modeling methods in OPNET simulations of Tactical Command and ...
Modeling methods in OPNET simulations of Tactical Command and ...
Modeling methods in OPNET simulations of Tactical Command and ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Model<strong>in</strong>g</strong> <strong>methods</strong> <strong>in</strong> <strong>OPNET</strong> <strong>simulations</strong> <strong>of</strong> <strong>Tactical</strong> <strong>Comm<strong>and</strong></strong> <strong>and</strong> Control<br />
Information Systems<br />
J. Mohorko, M. Fras, Ž. Čučej<br />
Laboratory for Signal Process<strong>in</strong>g <strong>and</strong> Remote Control<br />
University <strong>of</strong> Maribor, Faculty <strong>of</strong> Electrical Eng<strong>in</strong>eer<strong>in</strong>g <strong>and</strong> Computer Science<br />
Smetanova ul. 17, SI-2000 Maribor, Slovenia<br />
Phone: +386 2 22071840 Fax: +386 2 2207272 E-mail: mohorko@uni-mb.si<br />
Keywords: MIP, C2IEDM, C2IS, Replication, <strong>OPNET</strong>, <strong>Tactical</strong> networks, Traffic model<strong>in</strong>g, Simulations, WLAN<br />
Abstract - Slovenia is a member <strong>of</strong> MIP (Multilateral<br />
Interoperability Programme), the task <strong>of</strong> which is to provide<br />
<strong>in</strong>terpretations <strong>of</strong> national C2IS systems for successfully<br />
harmoniz<strong>in</strong>g jo<strong>in</strong>t action by <strong>in</strong>ternational military<br />
peacekeep<strong>in</strong>g forces. Interpretability with<strong>in</strong> MIP is carriedout<br />
by a unified model based on controlled data replication<br />
between the databases <strong>of</strong> C2IS systems. Systematic IRIS<br />
Replication Mechanism s<strong>of</strong>tware (IRM) is used for data<br />
replication. This paper presents <strong>methods</strong> <strong>of</strong> measur<strong>in</strong>g <strong>and</strong><br />
analyz<strong>in</strong>g traffic that causes IRM. We designed an <strong>OPNET</strong><br />
model on the basis <strong>of</strong> the analyzed results that would be<br />
suitable for the purposes <strong>of</strong> tactical radio network simulation.<br />
1. INTRODUCTION<br />
Simulations by the model<strong>in</strong>g <strong>and</strong> analyz<strong>in</strong>g <strong>of</strong><br />
communication system’s characteristics, has become one<br />
<strong>of</strong> the ma<strong>in</strong> challenges when construct<strong>in</strong>g networks, <strong>and</strong><br />
the development <strong>of</strong> network devices <strong>and</strong> protocols. The<br />
Slovenian army also felt such needs, when it called for a<br />
national research project 1 , the object which was the<br />
optimization <strong>of</strong> tactical radio communication networks.<br />
This would represent <strong>in</strong>frastructure for a national <strong>Tactical</strong><br />
<strong>Comm<strong>and</strong></strong> <strong>and</strong> Control Information System - C2IS<br />
(TISPINK <strong>in</strong> the Slovene language). Slovenian TISPINK<br />
is a member <strong>of</strong> the Multilateral Interoperability<br />
Programme (MIP), the mission <strong>of</strong> which is to ensure the<br />
<strong>in</strong>terpretability <strong>of</strong> national C2IS systems for harmoniz<strong>in</strong>g<br />
the activities <strong>of</strong> <strong>in</strong>ternational forces <strong>in</strong> jo<strong>in</strong>t peacekeep<strong>in</strong>g<br />
operations. Connectivity with<strong>in</strong> MIP enables a unified<br />
<strong>Comm<strong>and</strong></strong> <strong>and</strong> Control Information Exchange Data Model<br />
(C2IEDM), which is based a controlled replication <strong>of</strong> data<br />
between the C2IS system’s databases. The s<strong>of</strong>tware<br />
environment <strong>of</strong> Slovenian TISPINK is based two products<br />
from the Danish s<strong>of</strong>tware producer Systematic; these are<br />
Sitaware <strong>and</strong> IRM (IRIS Repliacation Mechanism).<br />
Sitaware represents graphic <strong>in</strong>terface for: the entry <strong>of</strong> data<br />
<strong>in</strong> to the C2IS database, GIS, <strong>and</strong> the plann<strong>in</strong>g <strong>and</strong> analysis<br />
<strong>of</strong> tactical operations <strong>in</strong> the field. IRM enables a controlled<br />
exchange <strong>of</strong> data between tactical units on the battlefield<br />
[1, 2, 3 ].<br />
<strong>OPNET</strong> is one <strong>of</strong> most powerful simulation tools for the<br />
analysis, plann<strong>in</strong>g <strong>and</strong> optimization <strong>of</strong> communication<br />
networks, devices <strong>and</strong> protocols. The best known use <strong>of</strong><br />
<strong>OPNET</strong> <strong>in</strong> the defense area orig<strong>in</strong>ates through the<br />
NETWARS programme <strong>of</strong> the US Department <strong>of</strong> Defense<br />
[5, 6,7].<br />
1 Target research programmes "Science for Peace <strong>and</strong> Security”:<br />
M2-0140 - <strong>Model<strong>in</strong>g</strong> <strong>of</strong> <strong>Comm<strong>and</strong></strong> <strong>and</strong> Control <strong>in</strong>formation<br />
systems, f<strong>in</strong>anced by Slovenian M<strong>in</strong>istry for Defense.<br />
This paper presents a segment <strong>of</strong> the outcome regard<strong>in</strong>g<br />
the research <strong>of</strong> our project. The goal is to develop <strong>methods</strong><br />
for the model<strong>in</strong>g <strong>of</strong> data traffic <strong>in</strong> a tactical network that is<br />
the consequence <strong>of</strong> the IRIS replication mechanism’s<br />
activity. The 2nd section briefly <strong>in</strong>troduces the <strong>OPNET</strong><br />
simulation package <strong>and</strong> its capabilities for evaluat<strong>in</strong>g<br />
telecommunication systems. Section 3 follows, which<br />
describes how to build a laboratorial model <strong>of</strong> the<br />
TISPINK system, where radio connections are replaced by<br />
Ethernet network. Ethernet traffic, captured by us<strong>in</strong>g the<br />
Ethereal network protocol analyzer, was analyzed us<strong>in</strong>g an<br />
ACE (Application Characterization Environment) module<br />
<strong>of</strong> <strong>OPNET</strong>. In section 4 tests <strong>and</strong> evaluates some <strong>of</strong> the<br />
<strong>OPNET</strong> traffic model<strong>in</strong>g <strong>methods</strong> suitable for our case.<br />
The results are summarized <strong>in</strong> section 5.<br />
2. <strong>OPNET</strong> OVERWIEW<br />
<strong>OPNET</strong> is a lead<strong>in</strong>g tool for simulat<strong>in</strong>g <strong>and</strong> evaluat<strong>in</strong>g<br />
telecommunication systems. It was presented for the first<br />
time to the communication <strong>in</strong>dustry <strong>in</strong> 1986.<br />
Fig. 1: <strong>OPNET</strong> with Project Editor, Node Editor <strong>and</strong> C-Source<br />
code Editor.
The basis is on object-oriented simulation approach<br />
supported by a series <strong>of</strong> graphic user <strong>in</strong>terface - editors<br />
(see Fig.1), which rather simplify the process <strong>of</strong><br />
communication networks model<strong>in</strong>g, devices, <strong>and</strong><br />
protocols. The project Editor enables the entry <strong>of</strong> graphic<br />
description <strong>of</strong> network topology. The Node Editor is used<br />
for describ<strong>in</strong>g protocols, <strong>and</strong> the connections between<br />
them, by us<strong>in</strong>g layers <strong>of</strong> the ISO/OSI model for<br />
communication devices. The Process Editor is an<br />
extension <strong>of</strong> programm<strong>in</strong>g language C. It uses a powerful<br />
f<strong>in</strong>ite-state mach<strong>in</strong>e (FSM) approach to represent <strong>of</strong><br />
different communication algorithms <strong>and</strong> protocols. The<br />
activity <strong>of</strong> <strong>in</strong>dividual state <strong>in</strong> FSM is implemented by<br />
programm<strong>in</strong>g language C. <strong>OPNET</strong> <strong>in</strong>corporates a lot <strong>of</strong><br />
already-prepared simulation models <strong>of</strong> st<strong>and</strong>ard<br />
communication equipment <strong>and</strong> protocols for wired, radio<br />
<strong>and</strong> optical transmission mediums. [4].<br />
2.1 <strong>OPNET</strong> module ACE<br />
<strong>OPNET</strong> is designed modularly. One <strong>of</strong> modules, used <strong>in</strong><br />
this study case, is ACE (Application Characterization<br />
Environment) [4]. ACE is a tool for the visualization,<br />
analysis <strong>and</strong> prediction <strong>of</strong> traffic <strong>in</strong> network applications.<br />
It helps us with the activity analysis <strong>of</strong> exist<strong>in</strong>g, <strong>and</strong> the<br />
development <strong>of</strong> new applications. This module allows the<br />
import<strong>in</strong>g <strong>of</strong> captured traffic by sniffer <strong>and</strong> analysis for the<br />
follow<strong>in</strong>g <strong>in</strong>tentions:<br />
• Diagnos<strong>in</strong>g application problems<br />
• Predict<strong>in</strong>g application behavior<br />
2.2 <strong>Model<strong>in</strong>g</strong> <strong>of</strong> network traffic by <strong>OPNET</strong><br />
The <strong>OPNET</strong> modeler allows for two basic <strong>methods</strong> <strong>of</strong><br />
network traffic model<strong>in</strong>g: explicit traffic <strong>and</strong> background<br />
traffic. For Explicit traffic, <strong>OPNET</strong> produces every packet<br />
separately. This method <strong>of</strong> network traffic generation also<br />
calls packet by packet traffic. In this manner the traffic <strong>of</strong><br />
the real system is clearly imitated, however such<br />
simulation is more numerically dem<strong>and</strong><strong>in</strong>g. These three<br />
<strong>methods</strong> for model<strong>in</strong>g explicit traffic:<br />
• Packets generator by which model<strong>in</strong>g on the<br />
network node determ<strong>in</strong>es the streams <strong>of</strong> packets<br />
exactly.<br />
• Application dem<strong>and</strong>s assign traffic between two<br />
network nodes.<br />
• Applications traffic model where traffic is generated<br />
by st<strong>and</strong>ard application models.<br />
Background traffic is analytically modeled traffic,<br />
which has an <strong>in</strong>fluence on the properties <strong>of</strong> a system <strong>in</strong> the<br />
form <strong>of</strong> additional delay. Background traffic can also be<br />
used <strong>in</strong> comb<strong>in</strong>ation with explicit traffic. <strong>OPNET</strong> allows<br />
the follow<strong>in</strong>g <strong>methods</strong> for model<strong>in</strong>g background traffic:<br />
• Traffic flow describes f<strong>in</strong>ite end-to-end traffic from<br />
source node to dest<strong>in</strong>ation node.<br />
• Basel<strong>in</strong>e loads represent background traffic on one<br />
<strong>of</strong> the selected l<strong>in</strong>ks (or from the node).<br />
• Application dem<strong>and</strong>s can also be used to represent<br />
background traffic between two nodes.<br />
(represent<strong>in</strong>g tactical units), as shown <strong>in</strong> Figure 2. C2IS<br />
database, Sitaware user <strong>in</strong>terface <strong>and</strong> IRIS replication<br />
mechanism are <strong>in</strong>stalled on every station. All stations are<br />
connected, over hub, <strong>in</strong> Ethernet network, which replaces<br />
radio network. The network is, on IP level, distributed<br />
over two subnets: broadcast <strong>and</strong> peer-to-peer. Stations <strong>in</strong><br />
subnets are def<strong>in</strong>ed us<strong>in</strong>g IP addresses, as shown <strong>in</strong> Table<br />
1. Another computer with <strong>in</strong>stalled s<strong>of</strong>tware Ethereal for<br />
captur<strong>in</strong>g Ethernet traffic (sniffer) was added to this rest<br />
network.<br />
Fig. 2: Block scheme <strong>of</strong> TISPINK test system.<br />
Unit IP address Peer-topeer<br />
Broadcast<br />
1.Brigade 192.168.1.1 x<br />
20.Battalion 192.168.20.1 x<br />
10.Battalion 192.168.10.1 x x<br />
1. Company 192.168.10.11 x<br />
2. Company 192.168.10.12 x<br />
Table 1: Logical distribution <strong>of</strong> units <strong>in</strong> test systems TISPINK<br />
with two subnets Peer-to-peer <strong>in</strong> Broadcast<br />
Data traffic, between stations <strong>in</strong> test network, is def<strong>in</strong>ed<br />
by contracts which are established by the IRIS replication<br />
mechanism. A contract def<strong>in</strong>es data contents <strong>and</strong><br />
dest<strong>in</strong>ations, where the data will be transmitted. Data<br />
contents are modeled by data sources (GPS, VoIP, manual<br />
entry, electronic mail, etc), which cause these contents.<br />
Contracts were divide by consider<strong>in</strong>g the dest<strong>in</strong>ations,<br />
which are addressed on certa<strong>in</strong> unit (peer-to-peer) <strong>and</strong><br />
contracts, which are addressed on all units with<strong>in</strong> the same<br />
subnet (broadcast).<br />
3. MEASURING AND ANALYSIS OF TISPINK<br />
TRAFFIC IN <strong>OPNET</strong><br />
A test laboratorial model <strong>of</strong> the TISPINK system was<br />
built. This test network is composed <strong>of</strong> five workstations<br />
Fig. 3: Measur<strong>in</strong>g <strong>of</strong> traffic with sniffer Ethereal
Data traffic occurs between <strong>in</strong>dividual units, when the<br />
IRM mechanism detects any change <strong>in</strong> the database. If<br />
there is a contract that refers to changed data, then this data<br />
will be sent to the dest<strong>in</strong>ation address. With the help <strong>of</strong><br />
SITAWARE GIS user-<strong>in</strong>terface, we moved <strong>of</strong> unit on<br />
fieldwork. The traffic caused by movement is measured<br />
us<strong>in</strong>g the Ethernet sniffer, as shown <strong>in</strong> Figure 3.<br />
Measur<strong>in</strong>g acquires the follow<strong>in</strong>g <strong>in</strong>formation about<br />
network traffic: time <strong>of</strong> generat<strong>in</strong>g packets, size <strong>of</strong> packets,<br />
type <strong>of</strong> protocol, <strong>in</strong>ter-arrival time, source IP, <strong>and</strong> the<br />
dest<strong>in</strong>ation IP address.<br />
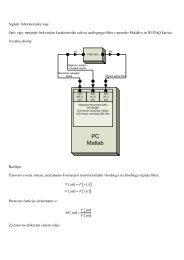
analyses, <strong>of</strong> captured traffic, we can use mathematical<br />
fitt<strong>in</strong>g tools such as EasyFit, as shown <strong>in</strong> Figure 6.<br />
With the help <strong>of</strong> the described tools, we can analyze<br />
measured traffic, which was caused by different activity<br />
conditions (broadcast <strong>and</strong> peer-to-peer) for IRM<br />
application <strong>in</strong> the tactical test network.<br />
Fig. 6: Tool for choos<strong>in</strong>g the distribution function <strong>and</strong> its<br />
parameters.<br />
4. SIMULATION RESULTS<br />
Fig. 4: Entry measure (captured) <strong>of</strong> traffic <strong>in</strong> the ACE module<br />
Us<strong>in</strong>g the <strong>OPNET</strong> ACE module the impact <strong>of</strong> different<br />
parameters was analyzed such as, for <strong>in</strong>stance, the<br />
b<strong>and</strong>width on delay <strong>in</strong> the network. First the captured<br />
traffic <strong>in</strong> the Ace Module was imported. Then the ACE<br />
module created a hierarchical picture <strong>of</strong> the network, as<br />
shown <strong>in</strong> Figure 4, where data connections between<br />
participants <strong>in</strong> tactical networks can also be seen. Stations<br />
<strong>in</strong> the network were named by IP addresses. The station <strong>in</strong><br />
Figure 4 with the IP number 192.168.10.255 is virtual<br />
station, which <strong>in</strong>troduces the broadcast IP address.<br />
The Data Exchange chart is used for analysis <strong>of</strong> traffic<br />
<strong>and</strong> packets <strong>of</strong> captured traffic, <strong>and</strong> <strong>of</strong>fers the exam<strong>in</strong>ation<br />
<strong>of</strong> time-dependence execution regard<strong>in</strong>g protocol between<br />
participant transmitt<strong>in</strong>g stations. In the case <strong>of</strong> such a<br />
graph with enlarged detail is shown Figure 5.<br />
<strong>OPNET</strong> allows the model<strong>in</strong>g <strong>of</strong> two types <strong>of</strong> traffic:<br />
explicit traffic <strong>and</strong> background traffic. In the explicit case,<br />
the traffic is modeled packet by packet. This is opposite to<br />
background traffic, which is analytically described <strong>and</strong> has<br />
an effect on network performance with additional delays.<br />
The analysis <strong>of</strong> traffic <strong>in</strong> the previous section enables the<br />
study<strong>in</strong>g <strong>of</strong> different possibilities for traffic model<strong>in</strong>g by<br />
<strong>OPNET</strong> <strong>simulations</strong>.<br />
The traffic <strong>of</strong> application IRM will be model<strong>in</strong>g us<strong>in</strong>g<br />
explicit traffic, because <strong>of</strong> the dem<strong>and</strong>ed reliability. Three<br />
different <strong>methods</strong> <strong>of</strong> model<strong>in</strong>g exist: a traffic generator,<br />
application dem<strong>and</strong>s, <strong>and</strong> an application traffic model.<br />
4.1 Applications traffic model<br />
<strong>OPNET</strong> conta<strong>in</strong>s 16 st<strong>and</strong>ard-application traffic models<br />
(as shown <strong>in</strong> Figure 7), which can be used on the<br />
follow<strong>in</strong>g node models (stations): WLAN workstation,<br />
MANET workstation <strong>and</strong> Ethernet workstation.<br />
Fig. 5: More detailed display <strong>of</strong> one movement <strong>of</strong> the unit <strong>and</strong><br />
generated packets <strong>of</strong> IRM application<br />
In <strong>OPNET</strong> we <strong>of</strong>ten model traffic, which is def<strong>in</strong>ed<br />
statistically with probability distributions for bit rate <strong>and</strong><br />
time between packets (<strong>in</strong>ter arrival time). For such<br />
Fig.7: St<strong>and</strong>ard applications <strong>in</strong> <strong>OPNET</strong>.
Parameters can be changed for every model <strong>of</strong><br />
application <strong>in</strong> regard to: size <strong>of</strong> packets, amount <strong>of</strong> packets<br />
(data rate), transport protocol, number <strong>of</strong> repeated send<strong>in</strong>g,<br />
timeouts, retransmissions, failure <strong>and</strong> recovery, etc. In<br />
addition, to us<strong>in</strong>g st<strong>and</strong>ard applications we can also model<br />
new 'custom' applications. We modeled a custom<br />
application with the help <strong>of</strong> the results derived from the<br />
ACE analysis described <strong>in</strong> the previous section.<br />
4.2 Application dem<strong>and</strong>s<br />
Applications dem<strong>and</strong> is a way <strong>of</strong> traffic model<strong>in</strong>g, where<br />
the application’s behavior is modeled. Dem<strong>and</strong>s<br />
characterize traffic by the sizes <strong>and</strong> rates <strong>of</strong> the requests<br />
<strong>and</strong> responses, between two nodes <strong>in</strong> both directions.<br />
considered criteria we decided that the traffic <strong>of</strong> IRM<br />
application would be modeled us<strong>in</strong>g traffic generators on a<br />
MANET station. This traffic generator does not have the<br />
possibility <strong>of</strong> def<strong>in</strong><strong>in</strong>g statistics for the ON/OFF process,<br />
which is a disadvantage <strong>of</strong> the traffic generator. This is the<br />
reasons why we were forced to change the <strong>in</strong>terpretation <strong>of</strong><br />
a traffic generator’s activity mechanism. In the new<br />
<strong>in</strong>terpretation we treat one packet as one transaction <strong>of</strong> the<br />
IRIS replication mechanism, where the new size <strong>of</strong> the<br />
packet is the sum <strong>of</strong> the transaction’s packets. We <strong>in</strong>terpret<br />
time between packets as time between <strong>in</strong>dividual<br />
transactions. Every MANET station enables the<br />
simultaneously activity <strong>of</strong> arbitrarily number <strong>of</strong> the traffic<br />
generators. For each <strong>of</strong> them, we can def<strong>in</strong>e dest<strong>in</strong>ation<br />
address (peer-to-peer or broadcast) <strong>and</strong> statistical<br />
descriptions <strong>of</strong> packet size <strong>and</strong> <strong>in</strong>ter-arrival time.<br />
Fig. 8: <strong>Model<strong>in</strong>g</strong> applications dem<strong>and</strong> between station <strong>and</strong><br />
server.<br />
4.3 Traffic generator<br />
We can model network traffic by a traffic generator,<br />
where the traffic is described statistically by packet size<br />
<strong>and</strong> time between packets (<strong>in</strong>ter arrival time). There are<br />
approximately 20 different probability distributions<br />
available.<br />
Traffic generators <strong>in</strong> <strong>OPNET</strong> are conta<strong>in</strong>ed <strong>in</strong> the<br />
follow<strong>in</strong>g node models (stations): Ethernet IP station, PPP<br />
IP station, MANET station. In some models (WLAN<br />
station <strong>in</strong> Figure 9) beside these two parameters, there is<br />
also the possibility <strong>of</strong> model<strong>in</strong>g the distribution <strong>of</strong><br />
probability for active <strong>and</strong> none-active states <strong>of</strong> the node<br />
(ON state <strong>and</strong> OFF state).<br />
5. CONCLUSION<br />
We modeled traffic <strong>of</strong> the IRM application <strong>in</strong> three<br />
different ways. Every method has certa<strong>in</strong> advantages <strong>and</strong><br />
disadvantages <strong>in</strong> its use. By choice, most suitable <strong>methods</strong><br />
consider the follow<strong>in</strong>g criteria: wireless station, mobility,<br />
consideration <strong>of</strong> terra<strong>in</strong> <strong>in</strong> the communication model,<br />
possibility <strong>of</strong> sett<strong>in</strong>g wireless LAN parameters for the<br />
model<strong>in</strong>g <strong>of</strong> radio devices, possibility <strong>of</strong> communication <strong>in</strong><br />
broadcast <strong>and</strong> peer-to-peer protocol. On the basis <strong>of</strong> the<br />
REFERENCES<br />
Fig. 9: <strong>Model<strong>in</strong>g</strong> <strong>of</strong> traffic by WLAN station<br />
[1] Multilateral Interoperability Programme, http://www.mipsite.org/<br />
[2] Sytematic, "IRIS Replication Mechanism", “White Paper”,<br />
Revision 1.16, December 2006<br />
[3] Sytematic, "SitaWare", “White Paper”, Revision 1.16,<br />
December 2006<br />
[4] <strong>OPNET</strong> Modeler, <strong>OPNET</strong> Technologies Inc.,<br />
http://www.opnet.com.<br />
[5] Steve L. Ferenci, C. Alspaugh, Efforts to Enhance<br />
Interoperability for Netwars, MILCOM 2004 - 2004 IEEE<br />
Military Communications Conference<br />
[6] William S. Murphy Jr., Mark A. Flournoy, "Simulat<strong>in</strong>g<br />
crises communications", Proceed<strong>in</strong>gs <strong>of</strong> the 2002 W<strong>in</strong>ter<br />
Simulation Conference, 954-959<br />
[7] V. Lakshm<strong>in</strong>arayan, "NETWARS St<strong>and</strong>ards Architecture<br />
<strong>and</strong> Implementation Issues" NETWARS St<strong>and</strong>ards<br />
Work<strong>in</strong>g Group. 1998