You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
FEATURE<br />
Do I need to take my shoes off?<br />
There is little doubt that air<br />
transport is far more secure<br />
following the tragic events of<br />
9/11. Still, from a passenger<br />
viewpoint, the security process<br />
has too often become intrusive,<br />
intimidating, and inconsistent.<br />
Long lines, pat downs, and<br />
constant packing and unpacking<br />
blight many a journey. From<br />
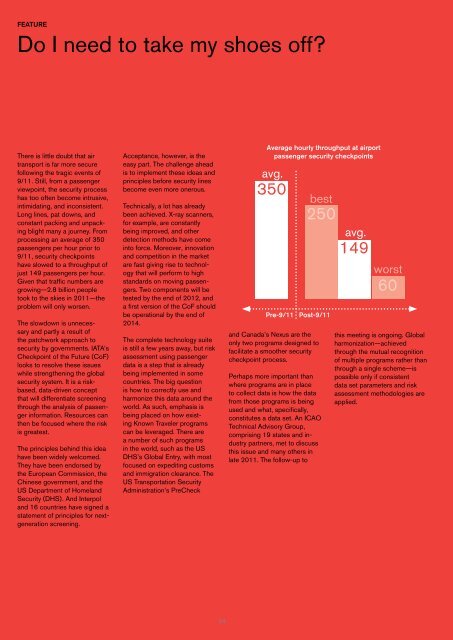
processing an average of 350<br />
passengers per hour prior to<br />
9/11, security checkpoints<br />
have slowed to a throughput of<br />
just 149 passengers per hour.<br />
Given that traffic numbers are<br />
growing—2.8 billion people<br />
took to the skies in 2011—the<br />
problem will only worsen.<br />
The slowdown is unnecessary<br />
and partly a result of<br />
the patchwork approach to<br />
security by governments. <strong>IATA</strong>’s<br />
Checkpoint of the Future (CoF)<br />
looks to resolve these issues<br />
while strengthening the global<br />
security system. It is a riskbased,<br />
data-driven concept<br />
that will differentiate screening<br />
through the analysis of passenger<br />
information. Resources can<br />
then be focused where the risk<br />
is greatest.<br />
The principles behind this idea<br />
have been widely welcomed.<br />
They have been endorsed by<br />
the European Commission, the<br />
Chinese government, and the<br />
US Department of Homeland<br />
Security (DHS). And Interpol<br />
and 16 countries have signed a<br />
statement of principles for nextgeneration<br />
screening.<br />
Acceptance, however, is the<br />
easy part. The challenge ahead<br />
is to implement these ideas and<br />
principles before security lines<br />
become even more onerous.<br />
Technically, a lot has already<br />
been achieved. X-ray scanners,<br />
for example, are constantly<br />
being improved, and other<br />
detection methods have come<br />
into force. Moreover, innovation<br />
and competition in the market<br />
are fast giving rise to technology<br />
that will perform to high<br />
standards on moving passengers.<br />
Two components will be<br />
tested by the end of <strong>2012</strong>, and<br />
a first version of the CoF should<br />
be operational by the end of<br />
2014.<br />
The complete technology suite<br />
is still a few years away, but risk<br />
assessment using passenger<br />
data is a step that is already<br />
being implemented in some<br />
countries. The big question<br />
is how to correctly use and<br />
harmonize this data around the<br />
world. As such, emphasis is<br />
being placed on how existing<br />
Known Traveler programs<br />
can be leveraged. There are<br />
a number of such programs<br />
in the world, such as the US<br />
DHS’s Global Entry, with most<br />
focused on expediting customs<br />
and immigration clearance. The<br />
US Transportation Security<br />
Administration’s PreCheck<br />
24<br />
Average hourly throughput at airport<br />
passenger security checkpoints<br />
avg.<br />
350<br />
Pre-9/11 Post-9/11<br />
and Canada’s Nexus are the<br />
only two programs designed to<br />
facilitate a smoother security<br />
checkpoint process.<br />
best<br />
250<br />
Perhaps more important than<br />
where programs are in place<br />
to collect data is how the data<br />
from those programs is being<br />
used and what, specifically,<br />
constitutes a data set. An ICAO<br />
Technical Advisory Group,<br />
comprising 19 states and industry<br />
partners, met to discuss<br />
this issue and many others in<br />
late 2011. The follow-up to<br />
avg.<br />
149<br />
worst<br />
60<br />
this meeting is ongoing. Global<br />
harmonization—achieved<br />
through the mutual recognition<br />
of multiple programs rather than<br />
through a single scheme—is<br />
possible only if consistent<br />
data set parameters and risk<br />
assessment methodologies are<br />
applied.