Elektronika 2009-11.pdf - Instytut Systemów Elektronicznych
Elektronika 2009-11.pdf - Instytut Systemów Elektronicznych
Elektronika 2009-11.pdf - Instytut Systemów Elektronicznych
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
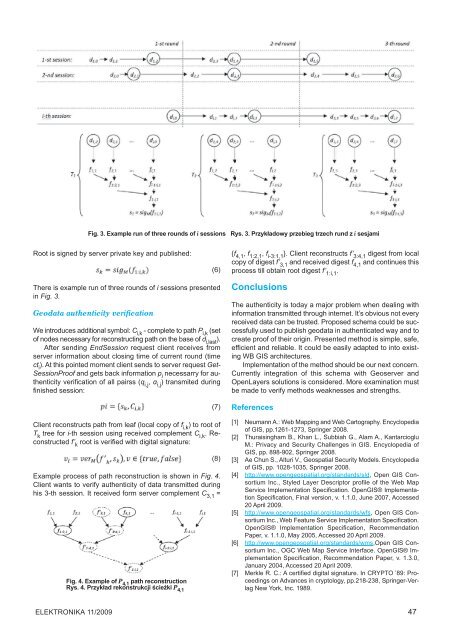
Fig. 3. Example run of three rounds of i sessions<br />
Rys. 3. Przykładowy przebieg trzech rund z i sesjami<br />
Root is signed by server private key and published:<br />
(6)<br />
There is example run of three rounds of i sessions presented<br />
in Fig. 3.<br />
Geodata authenticity verification<br />
We introduces additional symbol: C i,k - complete to path P i,k (set<br />
of nodes necessary for reconstructing path on the base of d i,last ).<br />
After sending EndSession request client receives from<br />
server information about closing time of current round (time<br />
ct i ). At this pointed moment client sends to server request Get-<br />
SessionProof and gets back information p i necessarry for authenticity<br />
verification of all pairss (q i,j , α i,j ) transmited during<br />
finished session:<br />
(7)<br />
Client reconstructs path from leaf (local copy of f i,k ) to root of<br />
T k tree for i-th session using received complement C i,k . Reconstructed<br />
f’ k root is verified with digital signature:<br />
(8)<br />
Example process of path reconstruction is shown in Fig. 4.<br />
Client wants to verify authenticity of data transmitted during<br />
his 3-th session. It received form server complement C 3,1 =<br />
Fig. 4. Example of P 4,1 path reconstruction<br />
Rys. 4. Przykład rekonstrukcji ścieżki P 4,1<br />
{f 4,1 , f 1:2,1 , f i-3:1,1 }. Client reconstructs f’ 3:4,1 digest from local<br />
copy of digest f’ 3,1 and received digest f 4,1 and continues this<br />
process till obtain root digest f’ 1:i,1 .<br />
Conclusions<br />
The authenticity is today a major problem when dealing with<br />
information transmitted through internet. It’s obvious not every<br />
received data can be trusted. Proposed schema could be successfully<br />
used to publish geodata in authenticated way and to<br />
create proof of their origin. Presented method is simple, safe,<br />
efficient and reliable. It could be easily adapted to into existing<br />
WB GIS architectures.<br />
Implementation of the method should be our next concern.<br />
Currently integration of this schema with Geoserver and<br />
OpenLayers solutions is considered. More examination must<br />
be made to verify methods weaknesses and strengths.<br />
References<br />
[1] Neumann A.: Web Mapping and Web Cartography. Encyclopedia<br />
of GIS, pp.1261-1273, Springer 2008.<br />
[2] Thuraisingham B., Khan L., Subbiah G., Alam A., Kantarcioglu<br />
M.: Privacy and Security Challenges in GIS. Encyclopedia of<br />
GIS, pp. 898-902, Springer 2008.<br />
[3] Ae Chun S., Alturi V., Geospatial Security Models. Encyclopedia<br />
of GIS, pp. 1028-1035, Springer 2008.<br />
[4] http://www.opengeospatial.org/standards/sld, Open GIS Consortium<br />
Inc., Styled Layer Descriptor profile of the Web Map<br />
Service Implementation Specification. OpenGIS® Implementation<br />
Specification, Final version, v. 1.1.0, June 2007, Accessed<br />
20 April <strong>2009</strong>.<br />
[5] http://www.opengeospatial.org/standards/wfs, Open GIS Consortium<br />
Inc., Web Feature Service Implementation Specification.<br />
OpenGIS® Implementation Specification, Recommendation<br />
Paper, v. 1.1.0, May 2005, Accessed 20 April <strong>2009</strong>.<br />
[6] http://www.opengeospatial.org/standards/wms,Open GIS Consortium<br />
Inc., OGC Web Map Service Interface. OpenGIS® Implementation<br />
Specification, Recommendation Paper, v. 1.3.0,<br />
January 2004, Accessed 20 April <strong>2009</strong>.<br />
[7] Merkle R. C.: A certified digital signature. In CRYPTO ’89: Proceedings<br />
on Advances in cryptology, pp.218-238, Springer-Verlag<br />
New York, Inc. 1989.<br />
ELEKTRONIKA 11/<strong>2009</strong> 47