Policy 7230A - Department of Administration
Policy 7230A - Department of Administration
Policy 7230A - Department of Administration
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
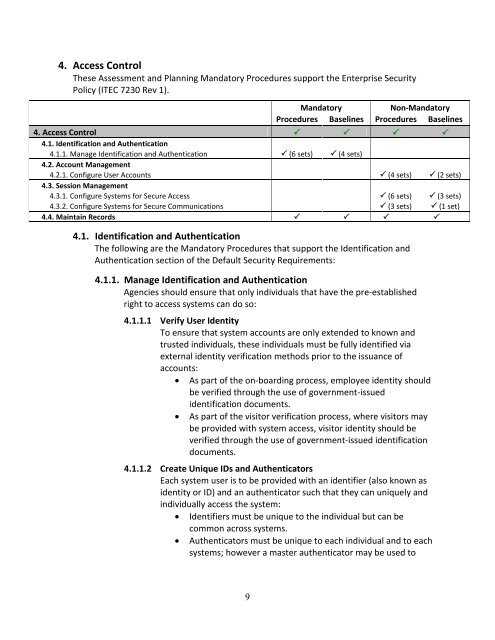
4. Access Control<br />
These Assessment and Planning Mandatory Procedures support the Enterprise Security<br />
<strong>Policy</strong> (ITEC 7230 Rev 1).<br />
Mandatory<br />
Non-Mandatory<br />
Procedures Baselines Procedures Baselines<br />
4. Access Control <br />
4.1. Identification and Authentication<br />
4.1.1. Manage Identification and Authentication (6 sets) (4 sets)<br />
4.2. Account Management<br />
4.2.1. Configure User Accounts (4 sets) (2 sets)<br />
4.3. Session Management<br />
4.3.1. Configure Systems for Secure Access (6 sets) (3 sets)<br />
4.3.2. Configure Systems for Secure Communications (3 sets) (1 set)<br />
4.4. Maintain Records <br />
4.1. Identification and Authentication<br />
The following are the Mandatory Procedures that support the Identification and<br />
Authentication section <strong>of</strong> the Default Security Requirements:<br />
4.1.1. Manage Identification and Authentication<br />
Agencies should ensure that only individuals that have the pre-established<br />
right to access systems can do so:<br />
4.1.1.1 Verify User Identity<br />
To ensure that system accounts are only extended to known and<br />
trusted individuals, these individuals must be fully identified via<br />
external identity verification methods prior to the issuance <strong>of</strong><br />
accounts:<br />
• As part <strong>of</strong> the on-boarding process, employee identity should<br />
be verified through the use <strong>of</strong> government-issued<br />
identification documents.<br />
• As part <strong>of</strong> the visitor verification process, where visitors may<br />
be provided with system access, visitor identity should be<br />
verified through the use <strong>of</strong> government-issued identification<br />
documents.<br />
4.1.1.2 Create Unique IDs and Authenticators<br />
Each system user is to be provided with an identifier (also known as<br />
identity or ID) and an authenticator such that they can uniquely and<br />
individually access the system:<br />
• Identifiers must be unique to the individual but can be<br />
common across systems.<br />
• Authenticators must be unique to each individual and to each<br />
systems; however a master authenticator may be used to<br />
9