Policy 7230A - Department of Administration
Policy 7230A - Department of Administration
Policy 7230A - Department of Administration
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
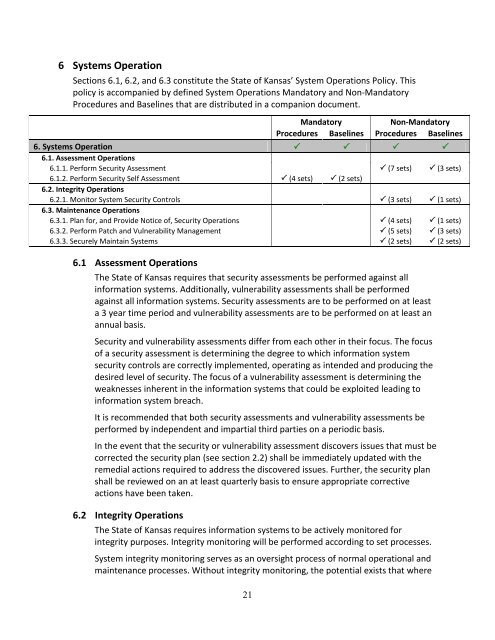
6 Systems Operation<br />
Sections 6.1, 6.2, and 6.3 constitute the State <strong>of</strong> Kansas’ System Operations <strong>Policy</strong>. This<br />
policy is accompanied by defined System Operations Mandatory and Non-Mandatory<br />
Procedures and Baselines that are distributed in a companion document.<br />
21<br />
Mandatory<br />
Non-Mandatory<br />
Procedures Baselines Procedures Baselines<br />
6. Systems Operation <br />
6.1. Assessment Operations<br />
6.1.1. Perform Security Assessment (7 sets) (3 sets)<br />
6.1.2. Perform Security Self Assessment (4 sets) (2 sets)<br />
6.2. Integrity Operations<br />
6.2.1. Monitor System Security Controls (3 sets) (1 sets)<br />
6.3. Maintenance Operations<br />
6.3.1. Plan for, and Provide Notice <strong>of</strong>, Security Operations (4 sets) (1 sets)<br />
6.3.2. Perform Patch and Vulnerability Management (5 sets) (3 sets)<br />
6.3.3. Securely Maintain Systems (2 sets) (2 sets)<br />
6.1 Assessment Operations<br />
The State <strong>of</strong> Kansas requires that security assessments be performed against all<br />
information systems. Additionally, vulnerability assessments shall be performed<br />
against all information systems. Security assessments are to be performed on at least<br />
a 3 year time period and vulnerability assessments are to be performed on at least an<br />
annual basis.<br />
Security and vulnerability assessments differ from each other in their focus. The focus<br />
<strong>of</strong> a security assessment is determining the degree to which information system<br />
security controls are correctly implemented, operating as intended and producing the<br />
desired level <strong>of</strong> security. The focus <strong>of</strong> a vulnerability assessment is determining the<br />
weaknesses inherent in the information systems that could be exploited leading to<br />
information system breach.<br />
It is recommended that both security assessments and vulnerability assessments be<br />
performed by independent and impartial third parties on a periodic basis.<br />
In the event that the security or vulnerability assessment discovers issues that must be<br />
corrected the security plan (see section 2.2) shall be immediately updated with the<br />
remedial actions required to address the discovered issues. Further, the security plan<br />
shall be reviewed on an at least quarterly basis to ensure appropriate corrective<br />
actions have been taken.<br />
6.2 Integrity Operations<br />
The State <strong>of</strong> Kansas requires information systems to be actively monitored for<br />
integrity purposes. Integrity monitoring will be performed according to set processes.<br />
System integrity monitoring serves as an oversight process <strong>of</strong> normal operational and<br />
maintenance processes. Without integrity monitoring, the potential exists that where