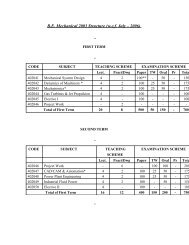
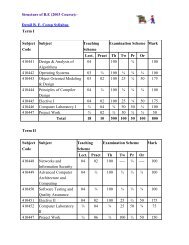
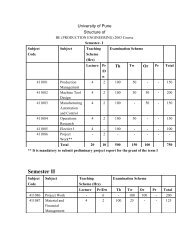
List of selected full length papers Paper ID Title - K. K. Wagh ...
List of selected full length papers Paper ID Title - K. K. Wagh ...
List of selected full length papers Paper ID Title - K. K. Wagh ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
134 UTILIZITION OF PEER-TO-PEER FILE SHARING ON GPRS NETWORK<br />
135 SMOIR: Scalable Multipurpose Ontology-based<br />
Information Retrieval system<br />
136 SECURE MUTUAL AUTHENTICATION AND CHEATING PREVENTION TECHNIQUE<br />
FOR REALTIME APPLICATIONS USING<br />
VISUAL CRYPTOGRAPHY<br />
137 Performance Analysis <strong>of</strong> Hierarchical Fault<br />
Tolerance Protocol for Mobile Agent Systems<br />
140 THREAT TO MOBILE BANKING ON iPhone (phishing)<br />
143 Data Mining Techniques To Facilitate The<br />
Integration Of Data In Data Warehouse<br />
144* Implementation <strong>of</strong> Hardware Stack TCP/IP using virtex-2 Pro FPGA<br />
146 Performance Improvement in Signature Detection Engine using Dual Algorithms<br />
150 Saving the World Unsolicited Email Flow<br />
151 A SURVEY OF BLACK HOLE ATTACK AND ITS SOLUTIONS<br />
IN MOBILE ADHOC NETWORKS.<br />
152 Implementation <strong>of</strong> Ethernet Controlled System<br />
157 3D Depth Perception from a Single Still Image<br />
159 WAVELET AND DCT BASED IMAGE AUTHENTICATION AND RECOVERY<br />
160 Reliable and failsafe service selection in dynamic distributed systems<br />
161 SECURITY ARCHITECTURE FOR MOBILE AD HOC<br />
NETWORKS<br />
164 Testing <strong>of</strong> Digital Controllers Using Real-Time Hardware in the Loop Simulation<br />
165 Doppler Estimation in Mobile Fading Channel<br />
168 VIRTUAL ADAPTIVE QUEUE MANAGEMENT (AQM):<br />
MANAGING BOTTLENECK QUEUE FROM NETWORK EDGE<br />
169 Energy Aware Routing Protocol for Wireless Sensor Networks<br />
171 Computational Model for Animation <strong>of</strong> Cloth Like<br />
Object<br />
173 Image Blending Techniques with application to<br />
Image Stitching<br />
175 Image Encryption Using Fusion <strong>of</strong> Image Inversion, Pixel Processing and Block-Based Transformation