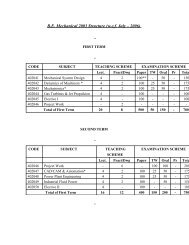
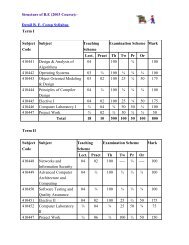
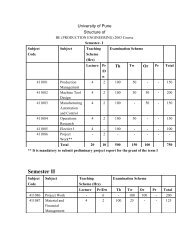
List of selected full length papers Paper ID Title - K. K. Wagh ...
List of selected full length papers Paper ID Title - K. K. Wagh ...
List of selected full length papers Paper ID Title - K. K. Wagh ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>List</strong> <strong>of</strong> <strong>selected</strong> <strong>full</strong> <strong>length</strong> <strong>papers</strong><br />
<strong>Paper</strong><br />
<strong>ID</strong> <strong>Title</strong><br />
1 Role <strong>of</strong> S<strong>of</strong>tware Agents in E-Commerce<br />
4 Taste Recognizer by Multi Sensor Electronic Tongue<br />
– a Case Study with Tea Quality Classification<br />
5 Low Pass Filtering and Computing Cost<br />
6 INTRA- GROUP LOAD BALANCING IN GR<strong>ID</strong> COMPUTING<br />
USING GENETIC ALGORITHM<br />
9 Service-Oriented Architecture for Collaborative Web Based Project<br />
Management S<strong>of</strong>tware<br />
11 Data Mining and Warehousing for Collaborative Web Based Educational<br />
Enterprise Resource Planning<br />
14 Designing Fractional Fourier Transform Architecture Using<br />
Systolic Array<br />
15 Speech Identification and Recognition Using Data Mining<br />
17 Relevance Feedback For CBIR using Image Processing<br />
18 Performance Study <strong>of</strong> bottleneck <strong>of</strong> Apriori and DIC Algorithm<br />
19 Virtual Memory Management on Demand Partition<br />
21 WEB CRAWLER<br />
AN INTELLIGENT AGENT<br />
22 S<strong>of</strong>tware Validation and Verification<br />
Practices in CMMI Levels &<br />
Introduction to CMMI V1.3<br />
25 Performance Analysis <strong>of</strong> Connected Component Based Image Text Detection Algorithm<br />
27 Building Pronunciation Dictionary for Telugu<br />
Language Automatic Speech Recognition system<br />
30 QUALITY ANALYSIS AND COMPARISON OF DCT BASED JPEG<br />
AND WAVELET BASED IMAGE COMPRESSION SCHEMES<br />
31 Performance Evaluation <strong>of</strong><br />
Low Energy Adaptive Clustering Hierarchy Protocol for Wireless Sensor Networks<br />
32 Throughput Maximization Routing For Location<br />
Based MANET<br />
33 Fast computation <strong>of</strong> marginalized walk kernel for Virtual Screening in Drug Discovery
34 Internet Usage Monitoring for Crime Detection<br />
36 BioBIKE<br />
Biological Integrated Knowledge Environment<br />
37 Agents : A View to Automated S<strong>of</strong>tware Engineering<br />
38 Deadlock-Free and Collision-Free<br />
Coordination Of Multiple Mobile Robots<br />
39 Face Images and Inferred Three-Dimensional Face Models used for Noncooperative Subject<br />
41 Wireless Charging for mobile Devices<br />
42 Comparative analysis <strong>of</strong> various Security techniques to protect<br />
VOIP system in an enterprise network<br />
43 Exploitation <strong>of</strong> Thread Level Parallelism and Instruction Level<br />
Parallelism using SMT in Superscalar Architecture<br />
48 Radar Target Tracking using Kalman Filter & Neural<br />
Netowrks<br />
49 Association Rule Mining Algorithms: A Literature Survey<br />
and a Comparative Study<br />
51 Intelligent Data Mining for Intrusion Detection System<br />
52 THRESHOLD BASED (k,n)IMAGE SECRET SHARING SCHME USING STEGANOGRAPHY<br />
53 Reducing branch cost with prediction using Load<br />
carrying Two-Bit predictor<br />
55 CONTENT-BASED IMAGE RETRIEVAL USING TEXTURE IN DIFFERENT COLOR MODELS<br />
56 Using XML and Databases<br />
57 OPTIMIZATION OF ROUTING IN WIRELESS SENSOR NETWORKS USING SWARM<br />
INTELLIGENCE<br />
59 An Interactive Environment for Clustering Dependent Tasks for<br />
Execution in Grid Environment<br />
60 IMPLEMENTATION OF AES ENCODER<br />
USING ACTIVE-HDL<br />
63 Brain Tumor Detection Using Segmentation<br />
Based on Fuzzy K-Means Algorithm<br />
68 AUTONOMOUS LIGHTWEIGHT AGENTS FOR INTRUSION<br />
DETECTION IN DISTRIBUTED SYSTEMS<br />
72 Watermarking Relational Databases
73 Unattended Installation and Un installation <strong>of</strong> S<strong>of</strong>twares Remotely<br />
74 Methodology for Speech Data Mining<br />
76 Data Mining using Collaborative Learning<br />
database<br />
77 Resolving Semantic Heterogeneity in<br />
Federated Database Systems<br />
78 CLUSTERING PROTOCOLS IN WIRELESS<br />
SENSOR NETWORKS<br />
80 Handling Churn Rate through a Structured<br />
Hierarchical Peer-to-Peer Overlay System<br />
86 Doppler Estimation in Mobile Fading Channel<br />
90 A Novel Approach: Data Hiding and Security <strong>of</strong> Multimedia<br />
Content using Steganography<br />
92 Resource Management in Wireless Adhoc<br />
Networks using Mobile Agents<br />
94 Roll In Roll Back Algorithm<br />
95 Wavelet and Histogram Based Methods for Content Based Image Retrieval<br />
97 Implementation <strong>of</strong> MTLRSA in SDLRLA Protocol<br />
99 Color Based Image Retrieval using Wavelet Transform and Neural Network Classification<br />
100 Cryptography techniques VS data obscuration for privacy preserving data mining<br />
101 FUZZY LOGIC IMPLEMENTATION FOR AVO<strong>ID</strong>ING COLLISION BETWEEN TRAINS<br />
103 An End To Website Content Piracy<br />
106 Development <strong>of</strong> wireless mesh network Emulation Model using EXATA<br />
108 QoS Based Framework For SOA<br />
109 Detection <strong>of</strong> Blood Count Related Diseases from Blood Cell Images<br />
114 Survey on Techniques for Data Stream Mining<br />
119 <strong>ID</strong>ENTIFICATION OF ANNUAL RINGS IN INDETERMINANT<br />
PLANTS USING DIFFERENT EDGE DETECTION METHODS<br />
121 Gene Silencing in Linkage Learning Genetic Algorithm<br />
127 Discovering Association Rules in Data Mining
134 UTILIZITION OF PEER-TO-PEER FILE SHARING ON GPRS NETWORK<br />
135 SMOIR: Scalable Multipurpose Ontology-based<br />
Information Retrieval system<br />
136 SECURE MUTUAL AUTHENTICATION AND CHEATING PREVENTION TECHNIQUE<br />
FOR REALTIME APPLICATIONS USING<br />
VISUAL CRYPTOGRAPHY<br />
137 Performance Analysis <strong>of</strong> Hierarchical Fault<br />
Tolerance Protocol for Mobile Agent Systems<br />
140 THREAT TO MOBILE BANKING ON iPhone (phishing)<br />
143 Data Mining Techniques To Facilitate The<br />
Integration Of Data In Data Warehouse<br />
144* Implementation <strong>of</strong> Hardware Stack TCP/IP using virtex-2 Pro FPGA<br />
146 Performance Improvement in Signature Detection Engine using Dual Algorithms<br />
150 Saving the World Unsolicited Email Flow<br />
151 A SURVEY OF BLACK HOLE ATTACK AND ITS SOLUTIONS<br />
IN MOBILE ADHOC NETWORKS.<br />
152 Implementation <strong>of</strong> Ethernet Controlled System<br />
157 3D Depth Perception from a Single Still Image<br />
159 WAVELET AND DCT BASED IMAGE AUTHENTICATION AND RECOVERY<br />
160 Reliable and failsafe service selection in dynamic distributed systems<br />
161 SECURITY ARCHITECTURE FOR MOBILE AD HOC<br />
NETWORKS<br />
164 Testing <strong>of</strong> Digital Controllers Using Real-Time Hardware in the Loop Simulation<br />
165 Doppler Estimation in Mobile Fading Channel<br />
168 VIRTUAL ADAPTIVE QUEUE MANAGEMENT (AQM):<br />
MANAGING BOTTLENECK QUEUE FROM NETWORK EDGE<br />
169 Energy Aware Routing Protocol for Wireless Sensor Networks<br />
171 Computational Model for Animation <strong>of</strong> Cloth Like<br />
Object<br />
173 Image Blending Techniques with application to<br />
Image Stitching<br />
175 Image Encryption Using Fusion <strong>of</strong> Image Inversion, Pixel Processing and Block-Based Transformation
176 Efficient Resource scheduling in Data Grid<br />
178 Advanced Intrusion Detection and Prevention<br />
System with Rule Based Mining Techniques and<br />
Using Prevention Policies over an Internet<br />
179 Hiding Sensitive Association Rules in Data Mining<br />
EARTH QUAKE AND FLOOD SENSOR SYSTEM<br />
<strong>ID</strong>ENTIFICATION OF ATTACK SURFACE IN CLOUD READY APPLICATION<br />
CROSS LAYER DESIGN FOR ROUTING & SECURITY IN MULTI-HOP WIRELESS NETWORKS<br />
Reversible Image Water Marking Using Integer Wavelet Transform<br />
Intrusion Detection in HomogeneousWireless Sensor Networks<br />
<strong>List</strong> <strong>of</strong> <strong>selected</strong> Poster <strong>papers</strong><br />
<strong>Paper</strong><br />
<strong>ID</strong> <strong>Title</strong><br />
7 Character Recognition: Performance Analysis<br />
20 On Demand Broadcasting: Efficient Mode<br />
45 Real-Time Human Computer Interaction with Feed Back States<br />
70 Determining Reliability <strong>of</strong> S<strong>of</strong>tware Products<br />
71 M-Commerce Security using Random LSB Steganography and Cryptography<br />
84 Web Site Quality Testing and User Satisfaction<br />
91 Discussion Forum: An Effective Tool for<br />
Information Retrieval<br />
93 Enterprise Application Security Using AOP-AspectJ<br />
96 Review <strong>of</strong> Optimization Tools Used for Cryptology<br />
98 DIGITAL WATERMARKING USING P4P<br />
104 Data Mining<br />
105 Investigating Attack Models against Navigation<br />
Oriented Personalization<br />
113 Authentication Protocol by modifying Kerberos Database<br />
115 Next Generation <strong>of</strong> Cellular Networks: WiMax 4G Technology: Broadband Wireless Access
118 Automatic License Plate Recognition System Using Neural Network<br />
120 Wavelet-Based Watermarking<br />
Algorithm Using Edge Detection<br />
124 Gain and Noise Figure measurement <strong>of</strong> Erbium-Doped Fiber Amplifier<br />
125 Finding Frequent Pattern And Temporal<br />
Association in Multivariate Time Series<br />
126 Pattern Recognition Using Advanced Error Back-propagation Methods<br />
128 Synchronization amongst Local Processes Using<br />
Hadoop in Cloud Computing<br />
129 A Survey <strong>of</strong> Content Based Multimedia Information Retrieval using Data Mining<br />
Techniques<br />
145 DIFFERENT MEASURES FOR ASSOSIATION RULE MINING<br />
147 NEED AND IMPLEMENTATION FOR FORENSIC READINESS IN CURRENT CORPORATE SCENERIO<br />
149 A High Performance Architecture For a Re-configurable Parallel DSP<br />
Processor<br />
154 Ontology based Intelligent Information Retrieval<br />
System<br />
167 Analysis <strong>of</strong> an Image Segmentation Strategies<br />
172 Wireless Sensor Network with Bluetooth<br />
180 Resource Sharing and Exchange <strong>of</strong> Information in Cloud<br />
181 Impact <strong>of</strong> Distributed Web Based Information System for Rural Healthcare<br />
Development<br />
182 IMAGE COMPRESSION USING WAVELETS<br />
Semantic Integrity Constraints<br />
in Parallel & Distributed Databases<br />
WiMAX Technology for Wireless Communication