OWASP Project:Secure Coding Quick Reference Guide
OWASP Project:Secure Coding Quick Reference Guide
OWASP Project:Secure Coding Quick Reference Guide
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
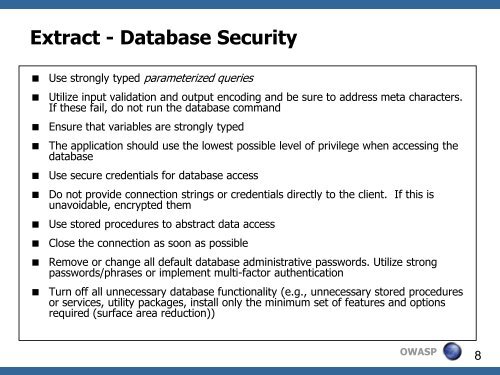
Extract - Database Security<br />
Use strongly typed parameterized queries<br />
Utilize input validation and output encoding and be sure to address meta characters.<br />
If these fail, do not run the database command<br />
Ensure that variables are strongly typed<br />
The application should use the lowest possible level of privilege when accessing the<br />
database<br />
Use secure credentials for database access<br />
Do not provide connection strings or credentials directly to the client. If this is<br />
unavoidable, encrypted them<br />
Use stored procedures to abstract data access<br />
Close the connection as soon as possible<br />
Remove or change all default database administrative passwords. Utilize strong<br />
passwords/phrases or implement multi-factor authentication<br />
Turn off all unnecessary database functionality (e.g., unnecessary stored procedures<br />
or services, utility packages, install only the minimum set of features and options<br />
required (surface area reduction))<br />
<strong>OWASP</strong><br />
8