An Ontology for Digital Forensics in IT Security Incidents - OPUS
An Ontology for Digital Forensics in IT Security Incidents - OPUS
An Ontology for Digital Forensics in IT Security Incidents - OPUS
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
20 CHAPTER 4. FORENSICS<br />
entry conta<strong>in</strong>s the name of a le, reference to correspond<strong>in</strong>g metadata<br />
entries and a list of le name entries <strong>for</strong> all children.<br />
• Metadata<br />
Similar to the le name entries there is at least one metadata entry<br />
<strong>for</strong> each le. This entry conta<strong>in</strong>s additional <strong>in</strong><strong>for</strong>mation <strong>for</strong> a le like<br />
access rights, ownership, access and creation times and additional ags.<br />
Furthermore it conta<strong>in</strong>s l<strong>in</strong>ks to le name entries and data units.<br />
• Application specific<br />
Some le system types allow special <strong>in</strong><strong>for</strong>mation like journals, quota<br />
restrictions, logs or other le system specic options.<br />
How the example from section 3.1 splits up to these categories is shown later<br />
<strong>in</strong> section 4.3.1 that expla<strong>in</strong>s the correspond<strong>in</strong>g tool.<br />
4.2.2 Random Access Memory<br />
Similar to the hard disk, the structure of the data <strong>in</strong> random access memory<br />
depends on the system it is managed by. A big dierence to the hard disk<br />
is that the random access memory is volatile. This means, its content is lost<br />
when the power is taken away from it.<br />
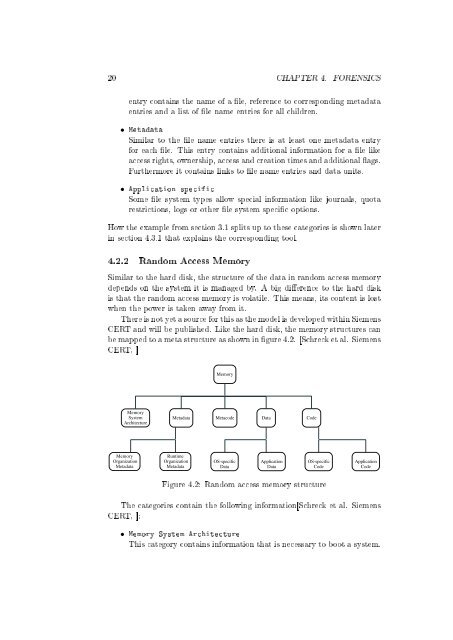
There is not yet a source <strong>for</strong> this as the model is developed with<strong>in</strong> Siemens<br />
CERT and will be published. Like the hard disk, the memory structures can<br />
be mapped to a meta structure as shown <strong>in</strong> gure 4.2. [Schreck et al. Siemens<br />
CERT, ]<br />
Memory<br />
Memory<br />
System<br />
Architecture<br />
Metadata<br />
Metacode<br />
Data<br />
Code<br />
Memory<br />
Organization<br />
Metadata<br />
Runtime<br />
Organization<br />
Metadata<br />
OS-specific<br />
Data<br />
Application<br />
Data<br />
OS-specific<br />
Code<br />
Application<br />
Code<br />
Figure 4.2: Random access memory structure<br />
The categories conta<strong>in</strong> the follow<strong>in</strong>g <strong>in</strong><strong>for</strong>mation[Schreck et al. Siemens<br />
CERT, ]:<br />
• Memory System Architecture<br />
This category conta<strong>in</strong>s <strong>in</strong><strong>for</strong>mation that is necessary to boot a system.