File Management - IBM
File Management - IBM File Management - IBM
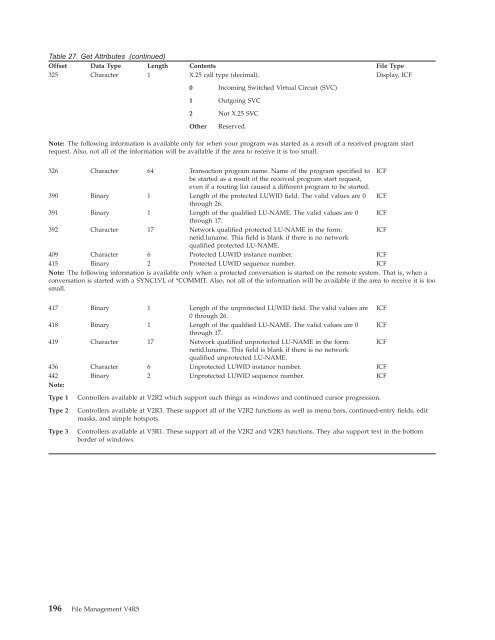
Table 27. Get Attributes (continued) Offset Data Type Length Contents File Type 325 Character 1 X.25 call type (decimal). Display, ICF 0 Incoming Switched Virtual Circuit (SVC) 1 Outgoing SVC 2 Not X.25 SVC Other Reserved. Note: The following information is available only for when your program was started as a result of a received program start request. Also, not all of the information will be available if the area to receive it is too small. 326 Character 64 Transaction program name. Name of the program specified to be started as a result of the received program start request, even if a routing list caused a different program to be started. ICF 390 Binary 1 Length of the protected LUWID field. The valid values are 0 through 26. ICF 391 Binary 1 Length of the qualified LU-NAME. The valid values are 0 through 17. ICF 392 Character 17 Network qualified protected LU-NAME in the form: netid.luname. This field is blank if there is no network qualified protected LU-NAME. ICF 409 Character 6 Protected LUWID instance number. ICF 415 Binary 2 Protected LUWID sequence number. ICF Note: The following information is available only when a protected conversation is started on the remote system. That is, when a conversation is started with a SYNCLVL of *COMMIT. Also, not all of the information will be available if the area to receive it is too small. 417 Binary 1 Length of the unprotected LUWID field. The valid values are 0 through 26. ICF 418 Binary 1 Length of the qualified LU-NAME. The valid values are 0 through 17. ICF 419 Character 17 Network qualified unprotected LU-NAME in the form: netid.luname. This field is blank if there is no network qualified unprotected LU-NAME. ICF 436 Character 6 Unprotected LUWID instance number. ICF 442 Note: Binary 2 Unprotected LUWID sequence number. ICF Type 1 Controllers available at V2R2 which support such things as windows and continued cursor progression. Type 2 Controllers available at V2R3. These support all of the V2R2 functions as well as menu bars, continued-entry fields, edit masks, and simple hotspots. Type 3 Controllers available at V3R1. These support all of the V2R2 and V2R3 functions. They also support text in the bottom border of windows. 196 File Management V4R5
Appendix B. Double-byte character set support This appendix contains information that you need if you use double-byte characters. This includes the following topics: v Double-byte character set (DBCS) fundamentals v Processing double-byte characters v Device file support v Display support v Copying files that contain double-byte characters v Writing application programs that process double-byte characters v DBCS font tables v DBCS sort tables v DBCS conversion dictionaries v Using DBCS conversion DBCS printer and spooling support information can be found in the Printer Device Programming book. Double-byte character set fundamentals Some languages, such as Chinese, Japanese, and Korean, have a writing scheme that uses many different characters that cannot be represented with single-byte codes. To create coded character sets for such languages, the system uses two bytes to represent each character. Characters that are encoded in two-byte code are called double-byte characters. Figure 17 on page 198 shows alphanumeric characters coded in a single-byte code scheme and double-byte characters coded in a double-byte code scheme. You can use double-byte characters as well as single-byte characters in one application. For instance, you may want to store double-byte data and single-byte data in your database, create your display screens with double-byte text and fields, or print reports with double-byte characters. © Copyright IBM Corp. 1998, 2000 197
- Page 156 and 157: - Description: This Field Definitio
- Page 158 and 159: Date Fields All date formats suppor
- Page 160 and 161: 150 File Management V4R5 Figure 14
- Page 162 and 163: devices that process the same type
- Page 164 and 165: Default system output queues 154 Fi
- Page 166 and 167: Spooling writers 156 File Managemen
- Page 168 and 169: value of *OWNER indicates that only
- Page 170 and 171: 160 File Management V4R5 You can us
- Page 172 and 173: 162 File Management V4R5 QFNC Finan
- Page 174 and 175: 164 File Management V4R5 If a job b
- Page 176 and 177: Spooling subsystem 166 File Managem
- Page 178 and 179: 168 File Management V4R5 the DLTSPL
- Page 180 and 181: Table 20. Open Feedback Area (conti
- Page 182 and 183: Table 20. Open Feedback Area (conti
- Page 184 and 185: Table 21. Device Definition List (c
- Page 186 and 187: Table 21. Device Definition List (c
- Page 188 and 189: Table 21. Device Definition List (c
- Page 190 and 191: Table 23. Common I/O Feedback Area
- Page 192 and 193: Table 23. Common I/O Feedback Area
- Page 194 and 195: Table 23. Common I/O Feedback Area
- Page 196 and 197: Table 24. I/O Feedback Area for ICF
- Page 198 and 199: Table 24. I/O Feedback Area for ICF
- Page 200 and 201: Table 26. I/O Feedback Area for Dat
- Page 202 and 203: Table 27. Get Attributes (continued
- Page 204 and 205: Table 27. Get Attributes (continued
- Page 208 and 209: (SBCS) A B 1 2 1-Byte Code X’C1
- Page 210 and 211: 200 File Management V4R5 Table 28.
- Page 212 and 213: Invalid double-byte code and undefi
- Page 214 and 215: DBCS device file support 204 File M
- Page 216 and 217: 206 File Management V4R5 - Create D
- Page 218 and 219: DBCS display support 208 File Manag
- Page 220 and 221: 210 File Management V4R5 When you c
- Page 222 and 223: DBCS font tables 212 File Managemen
- Page 224 and 225: 214 File Management V4R5 CPYIGCTBLI
- Page 226 and 227: DBCS font files DBCS sort tables 21
- Page 228 and 229: Finding out if a DBCS sort table ex
- Page 230 and 231: 220 File Management V4R5 v When you
- Page 232 and 233: User-created dictionary for DBCS 22
- Page 234 and 235: Work with DBCS conversion dictionar
- Page 236 and 237: another alphanumeric entry in the e
- Page 238 and 239: Figure 22. Display Produced by the
- Page 240 and 241: 230 File Management V4R5 1. Positio
- Page 242 and 243: Figure 23. Example Screen 1 Positio
- Page 244 and 245: Figure 27. Example Screen 5 234 Fil
- Page 246 and 247: 236 File Management V4R5 - If you t
- Page 248 and 249: contains information on data descri
- Page 250 and 251: 240 File Management V4R5
- Page 252 and 253: CHGWTR (Change Writer) command 157
- Page 254 and 255: command, CL 160, 212 (continued) Tr
Table 27. Get Attributes (continued)<br />
Offset Data Type Length Contents <strong>File</strong> Type<br />
325 Character 1 X.25 call type (decimal).<br />
Display, ICF<br />
0 Incoming Switched Virtual Circuit (SVC)<br />
1 Outgoing SVC<br />
2 Not X.25 SVC<br />
Other Reserved.<br />
Note: The following information is available only for when your program was started as a result of a received program start<br />
request. Also, not all of the information will be available if the area to receive it is too small.<br />
326 Character 64 Transaction program name. Name of the program specified to<br />
be started as a result of the received program start request,<br />
even if a routing list caused a different program to be started.<br />
ICF<br />
390 Binary 1 Length of the protected LUWID field. The valid values are 0<br />
through 26.<br />
ICF<br />
391 Binary 1 Length of the qualified LU-NAME. The valid values are 0<br />
through 17.<br />
ICF<br />
392 Character 17 Network qualified protected LU-NAME in the form:<br />
netid.luname. This field is blank if there is no network<br />
qualified protected LU-NAME.<br />
ICF<br />
409 Character 6 Protected LUWID instance number. ICF<br />
415 Binary 2 Protected LUWID sequence number. ICF<br />
Note: The following information is available only when a protected conversation is started on the remote system. That is, when a<br />
conversation is started with a SYNCLVL of *COMMIT. Also, not all of the information will be available if the area to receive it is too<br />
small.<br />
417 Binary 1 Length of the unprotected LUWID field. The valid values are<br />
0 through 26.<br />
ICF<br />
418 Binary 1 Length of the qualified LU-NAME. The valid values are 0<br />
through 17.<br />
ICF<br />
419 Character 17 Network qualified unprotected LU-NAME in the form:<br />
netid.luname. This field is blank if there is no network<br />
qualified unprotected LU-NAME.<br />
ICF<br />
436 Character 6 Unprotected LUWID instance number. ICF<br />
442<br />
Note:<br />
Binary 2 Unprotected LUWID sequence number. ICF<br />
Type 1 Controllers available at V2R2 which support such things as windows and continued cursor progression.<br />
Type 2 Controllers available at V2R3. These support all of the V2R2 functions as well as menu bars, continued-entry fields, edit<br />
masks, and simple hotspots.<br />
Type 3 Controllers available at V3R1. These support all of the V2R2 and V2R3 functions. They also support text in the bottom<br />
border of windows.<br />
196 <strong>File</strong> <strong>Management</strong> V4R5