Computer Forensics foredrag - Prosa
Computer Forensics foredrag - Prosa
Computer Forensics foredrag - Prosa
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
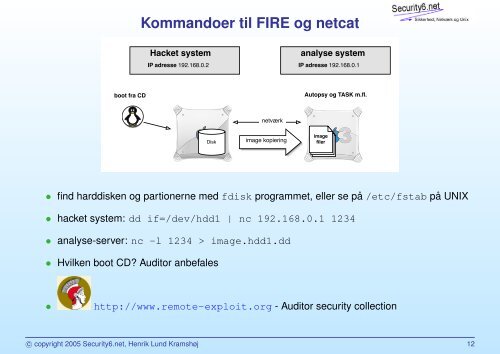
Kommandoer til FIRE og netcat<br />
Hacket system<br />
IP adresse 192.168.0.2<br />
analyse system<br />
IP adresse 192.168.0.1<br />
boot fra CD<br />
Autopsy og TASK m.fl.<br />
netværk<br />
Disk<br />
image kopiering<br />
image<br />
filer<br />
• find harddisken og partionerne med fdisk programmet, eller se på /etc/fstab på UNIX<br />
• hacket system: dd if=/dev/hdd1 | nc 192.168.0.1 1234<br />
• analyse-server: nc -l 1234 > image.hdd1.dd<br />
• Hvilken boot CD? Auditor anbefales<br />
• http://www.remote-exploit.org - Auditor security collection<br />
c○ copyright 2005 Security6.net, Henrik Lund Kramshøj 12





![Brug dit studieliv aktivt [s.8-15] - Prosa](https://img.yumpu.com/25535032/1/184x260/brug-dit-studieliv-aktivt-s8-15-prosa.jpg?quality=85)










